Creating Organizational Units (OUs)
Reasons to create OUs
Remember that OUs are used to structure data within an Active Directory. Typically, there are three reasons why you might need to create an OU:
- Segregate Objects: It is common practice to group related data into an OU. For example, user and computer objects are typically stored in separate containers.
- Delegate Administration: One of the primary reasons for creating an OU is to delegate administration. With OUs you can give a person or a group or people rights to perform certain administrative functions on objects within an OU.
- Appy GPO: An OU is the lowest-level container object that a GPO can be applied to. If you have different types of users within your organization that need to apply different GPOs, the easiest way to set that up is by storing the users in different OUs and apply GPOs accordingly.
How to create OUs?
To get started open your start menu and go to your "Apps" section. You can click the arrow pointing down, and it will take you to it. Click on "Active Directory users and Computers"
 |
| Figure 1. Start Menu. |
 |
| Figure 2. Apps Menu. Selecting Active Directory Users and Computers. |
You will see the default OUs on the right panel that belong to your root domain name.
 |
| Figure 3. Active Directory Users and Computers Console. |
Right click on your domain name > New > Organizational Unit.
 |
| Figure 4. Creating a new Organizational Unit. |
Give it a name. You can start off with something like locations or different departments in your fake/lab organization. It will be all up to you how you want to set this up. We can start creating a Marketing OU as shown in figure 5 below.
 |
| Figure 5. Naming our first OU. |
 |
| Figure 6. First OU created. |
How do you delete a protected OU?
- Click on View and enable Advanced Features
- Right click on the protected OU you want to delete and select properties
- Click on the tab name "object", and you will see that the checkbox for option "Protect object from deletion" is checked. All you have to do is click on the checkbox to disable that option.
- Click Apply and OK
- Now you can right click on the OU you just disable the "Protect object from deletion" option, and select Delete (Confirm you want to delete the OU by clicking yes on the warning message)
 |
| Figure 6. Enabling Advanced Features. |
 |
| Figure 7. Organizational Units panel. |
 |
| Figure 8. Marketing's Properties. |
 |
| Figure 9. Marketing OU properties. Protect object from accidental deletion. |
 |
| Figure 10. Marketing OU properties. Disabling "Protect object from accidental deletion". |
 |
| Figure 11. Deleting OU. |
 |
| Figure 12. Confirming deletion of OU. |
 |
| Figure 13. Marketing OU successfully deleted. |
Finally, if you want to have an idea on how you could organize your OUs in a similar way how an organization would do it, check figure 14 below. (I have seen several mid-sized organizations doing it like that). That's how I have mine set up.
 |
| Figure 14. OUs example. |
Creating Users
One way to create users is by using the same "Active Directory Users and Computers" console. Click on the OU you created to store domain users and right click on the right panel > select New > User option.
 |
| Figure 15. Creating users. |
Type the name of the new user, the user logon name and click Next.
 |
| Figure 16. Creating users. |
Type a password for your user, password properties and click Next.
 |
| Figure 17. Creating users. |
If you want your user to change his or her password at next logon, check the option "user must change password at next logon".
 |
| Figure 18. Creating users. |
 |
| Figure 19. user successfully created. |
There is another way to create users and it is through the new Active Directory Administrative Center console which I will show you later after creating a group. What you can try also, if you want to, is to follow a great article from Carlos Perez which shows you how to create real looking users accounts for your AD Lab (over 2000 users at once)
http://www.darkoperator.com/blog/2016/7/30/creating-real-looking-user-accounts-in-ad-lab
Creating Groups
Types of groups in Active Directory
- Distribution Groups: Used to create email distribution lists.
- Security Group: used to assign permissions to shared resources.
Group Scope
Groups are characterized by a score that identifies the extent to which the group is applied in the domain tree of forest. The scope of the group defines where the group can be granted permissions. [Source]
Scope
|
Possible Members
|
Scope Conversion
|
Can Grant Permissions
|
Possible Member of
|
|---|---|---|---|---|
Universal
|
Accounts from any domain in the same forest
Global groups from any domain in the same forest
Other Universal groups from any domain in the same forest
|
Can be converted to Domain Local scope
Can be converted to Global scope if the group does not contain any other Universal groups
|
On any domain in the same forest or trusting forests
|
Other Universal groups in the same forest
Domain Local groups in the same forest or trusting forests
Local groups on computers in the same forest or trusting forests
|
Global
|
Accounts from the same domain
Other Global groups from the same domain
|
Can be converted to Universal scope if the group is not a member of any other global group
|
On any domain in the same forest, or trusting domains or forests
|
Universal groups from any domain in the same forest
Other Global groups from the same domain
Domain Local groups from any domain in the same forest, or from any trusting domain
|
Domain Local
|
Accounts from any domain or any trusted domain
Global groups from any domain or any trusted domain
Universal groups from any domain in the same forest
Other Domain Local groups from the same domain
Accounts, Global groups, and Universal groups from other forests and from external domains
|
Can be converted to Universal scope if the group does not contain any other Domain Local groups
|
Within the same domain
|
Other Domain Local groups from the same domain
Local groups on computers in the same domain, excluding built-in groups that have well-known SIDs
|
Creating a new Security - Domain Local Group
One common security group that is created in organizations is the "Workstations Administrators" group, and even though we are trying to keep our environment as basic and vulnerable as possible, it is a good exercise to understand how groups and GPOs work together to access resources in your domain. Our security group can be used to allow IT staff log on on to workstations with administrative privileges. We can still enable built-in administrators (RID 500) accounts in our workstations to test simple pass-the-hash attacks in future posts.
Go back to your Active Directory Users and Computers console, and click on the OU where you want to store your new group. I created an OU named "Groups" and two sub-groups "Distribution" & "Security". Right click on the OU (in my case Security) > New > Group.
 |
| Figure 20. Creating new group. |
Based on the definitions provided above about group types and scopes, I created a Security Group with a Domain Local scope and named it " SG DL HF (domain name) Workstation Administrators"
 |
| Figure 21. Creating a new Security group - Domain Local scope. |
Create a new user and add him or her to the new group
Now that we have our security group created, we can add users to it. We can just edit the profile of an existing user and add him or her to the security group. However, this time I want to show you how you can create a user and add him or her to an existing group at the same time by using the new Active Directory Administrative Center.
To get started open your start menu and go to your "Apps" section. You can click the arrow pointing down, and it will take you to it. Click on "Active Directory Administrative center" as shown in figure 22 below.
 |
| Figure 22. Active Directory Administrative Center Menu App. |
 |
| Figure 23. Active Directory Administrative Center Overview. |
If we expand our root domain name hf on the left panel, we can see that we can still navigate through all our custom OUs the same way how we did it while creating them via the Active Directory Users and Computers console. For this exercise, I browsed to my HF OU > Users > Global IT organizational unit.
 |
| Figure 24. Navigating through OUs in Active Directory Administrative Center console. |
 |
| Figure 25. Selecting HF OU > Users > Global IT OU. |
Fill out the necessary fields to create the new user. As you can see, we already have more options than what we had by default from the Active Directory Users and Computers console.
 |
| Figure 26. Creating new user. |
Scroll down, and you will see even more options such as "Member Of" to add user to a group, Profile Paths, log on scripts and even authentication policies. We just click the option "Add" in the Member Of section, type our Security group name "SG DL HF Workstation Administrators", Click on Check names, and if the group exists, the name of our group gets underlined. Finally, click Ok and the user will be a member of that group as soon as it is created.
 |
| Figure 27. More options such as Member of, Directly Associated Password Settings and Authentication policies. |
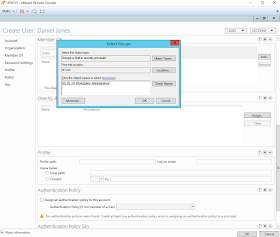 |
| Figure 28. Adding new user to a group. Security Group "Workstation Administrators". |
Click Ok again and the user will be created.
 |
| Figure 29. User settings configured and ready to be created. |
We already have a security group to store users that will be able to log on to computers with administrator privileges, but without a GPO with the right policy that allows users in that group log on to computers in the domain with administrator privileges, it will not work.
Creating Group Policy Objects (GPOs)
GPOs Overview
A Group Policy object (GPO) is a logical object composed of two components, a Group Policy container and a Group Policy template. Windows stores both of these objects on domain controllers in the domain. The Group Policy container object is stored in the domain partition of Active Directory. GPOs contain policy settings. You can think of GPOs as policy documents that apply their settings to the computers and users within their control.
Group Policy objects and their settings apply to computers and user to which they are linked. You can link GPOs to an Active Directory site, domain, organizational unit, or nested organizational unit. [Source]
Linking GPOs
Understanding Group Policy scope requires knowing where to link Group Policy objects so they apply to users or computer. To enable a Group Policy object to apply to a user or computer, you associate it with a specific location within Active Directory. Associating a Group Policy object with an object in Active Directory is called linking. Active Directory has rules that govern where you can link Group Policy objects. Active Directory objects to which you can link Group Policy objects include: [Source]
- Site objects
- Domain objects
- Organizational Unit objects
Setting up our Workstations Administrator GPO
To get started, open your start menu and go to your "Apps" section as shown in figure 1 and 2. Click on "Group Policy Management" and select the OU which the policy will be applied to. In this case since we are trying to have users logging on to computers in the network with administrator privileges, I select my "Clients" OU.
 |
| Figure 30. Group Policy Management Console. |
Right click on the OU, select "Create a GPO in this domain, and link it here.." and give it a name.
 |
| Figure 31. Creating a GPO on Clients OU. |
 |
| Figure 32. Naming our GPO. |
 |
| Figure 33. GPO successfully created but not configured yet. |
Configure your new GPO by right clicking on it and selecting Edit.
 |
| Figure 34. Editing new GPO. |
Once in the Group Policy Management Editor console, do the following:
- Expand Computer Configuration > Preferences > Control Panel Settings > Local Users and Groups
- As you can see in figure 35 below, there are not groups or users set up yet. Right click on it and select New > Local Group
- Set "Group Name" to Administrators (built-in)
- In the "Members Section", click on the option "Add"
- Look for the group you want to add to it. In our case, it will be our "SG DL HF Workstation Administrators"
- Click Ok, Ok , Apply and Ok again.
 |
| Figure 35. Adding a new local group to our new GPO. |
 |
| Figure 36. Selecting a specific group name . Administrators (Built-in). |
 |
| Figure 37. Group name set to Administrators (built-in). |
 |
| Figure 38. Adding a Local group member to the GPO. SG DL HF Workstation Administrator. |
 |
| Figure 39. Confirming addition of Local Group Member. |
 |
| Figure 40. New Local Group Properties. |
 |
| Figure 41. Applying changes. |
 |
| Figure 42. GPO edited successfully. |
Now, whenever you add a windows system to your domain and check the local administrator group members, you will see your Security group in it as shown in figure 43 below.
But how can I test this if I don't have computers joined to my domain? (First make sure that you have your Windows 7 boxes set up and with IP addresses leased by your own Windows Server 2012.)
Joining computers to our domain
Want to redirect computers joined to your domain to an specific OU?
Before we start joining computers to our domain, we can set a new default container location to store computers joining our domain. For this, you will just have to use the "redircmp" command and the "Distinguished Name (DN)" of the container that will become the default location for newly created computer objects.
 |
| Figure 44. Redirecting default container for computers being joined to the domain. |
Joining our first computer to our domain
As you can see in figure 45 below, our Windows 7 computer is not part our domain yet. It is part of a Workgroup named WORKGROUP. To get started click on "Change Settings"
Next, in the "Computer Name" section click on the option "Change". Select the option Domain and type the name of your domain. I typed hf.com and clicked Ok.
 |
| Figure 46. Adding our system to our hf.com domain. |
If for some reason you get the error in figure 47 below, make sure you can ping your DC and have your DC IP address as your primary DNS server.
 |
| Figure 47. Active Directory DC could not be contacted. |
If your system can communicate with the DC, you will get a prompt to enter privileged credentials. I entered the credentials of our user that has administrator privileges.
 |
| Figure 48. Credentials to join computer to the domain. |
If everything goes well, you will receive a welcome message to your domain.
 |
| Figure 49. Welcome to the hf.com domain. |
Next, click Ok and restart your system.
 |
| Figure 50. Restarting system to apply changes. |
After restarting your system, click on "Switch User" and select other user.
 |
| Figure 53. Switching user. |
You can see that our user will be automatically logging on to HF (our domain)
 |
| Figure 54. Logging onto HF. |
 |
| Figure 55. Logging onto HF. |
Now your computer will not longer be part of WORKGROUP. It will be part of the hf.com domain.
 |
| Figure 56. Domain hf.com. |
If you go back to your DC's Active Directory Users and Computers console, you will see that the computer that you just joined to the domain will show up inside of the OU we set earlier as the default container to store computers joining the domain. If it is not there, just refresh your console, and it should show up.
 |
| Figure 57. Computer showing inside of default container for computers joining the domain. |
If you want to go the extra mile and move your computer to another sub-OU, you can do it manually by selecting the computer and dragging it to the the right OU. Click yes and it will be moved to the set location. You can automate this with a script or Group Policy.
 |
| Figure 58. Moving computers to sub-containers. |
Awesome! so up to this point, we have most of the basic configurations of a domain setup taken care of. However, in order to increase the visibility on our domain endpoints from a logging perspective, it is important to create a more robust audit policy.
Creating a more robust Audit Policy
To get started open your Group Policy management console, right click on "Group Policy Objects", and select the options "New".
 |
| Figure 59. Creating new GPO. |
Give it a name. I named mine "Full Domain Auditing Policy" and click Ok.
 |
| Figure 60. Naming our new GPO. |
Right click on the new GPO and click on Edit.
 |
| Figure 61. Editing Full Domain Auditing Policy. |
Prior to Windows Server 2008, Windows auditing was limited to 9 items. [Source]
 |
| Figure 62. Default Audit Policy items. |
Starting with Windows Vista & Windows Server 2008, Windows auditing is expanded to 57 items. [Source]
 |
| Figure 63. Additional 57 items to the Audit Policy. |
Go back to your Local Policies > Audit Policy, right click on each item, select properties and define the policy settings by selecting the attempts you want to audit.
 |
| Figure 64. Editing items in Local Policies - Audit Policy |
 |
| Figure 65. Defining policy settings. |
 |
| Figure 66. First policy item set up successfully. |
Following Sean Metcalf's Full Domain Auditing Policy, I set up mine as shown in figure 67 below.
 |
| Figure 67. Local Policies - Default Audit Policy set up. |
Now, before setting up your additional 57 items of your "Full Domain Auditing Policy", I believe it is important to take a look at what Microsoft recommends:
Microsoft Recommendations:
| Audit Policy Category or Subcategory | Windows Default
Success Failure
| Baseline Recommendation
Success Failure
| Stronger Recommendation
Success Failure
|
|---|---|---|---|
| Account Logon | |||
| Audit Credential Validation | No No | Yes Yes | Yes Yes |
| Audit Kerberos Authentication Service | Yes Yes | ||
| Audit Kerberos Service Ticket Operations | Yes Yes | ||
| Audit Other Account Logon Events | Yes Yes | ||
| Account Management | |||
| Audit Application Group Management | |||
| Audit Computer Account Management | Yes DC | Yes Yes | |
| Audit Distribution Group Management | |||
| Audit Other Account Management Events | Yes Yes | Yes Yes | |
| Audit Security Group Management | Yes Yes | Yes Yes | |
| Audit User Account Management | Yes No | Yes Yes | Yes Yes |
| Detailed Tracking | |||
| Audit DPAPI Activity | Yes Yes | ||
| Audit Process Creation | Yes No | Yes Yes | |
| Audit Process Termination | |||
| Audit RPC Events | |||
| DS Access | |||
| Audit Detailed Directory Service Replication | |||
| Audit Directory Service Access | DC DC | DC DC | |
| Audit Directory Service Changes | DC DC | DC DC | |
| Audit Directory Service Replication | |||
| Logon and Logoff | |||
| Audit Account Lockout | Yes No | Yes No | |
| Audit User/Device Claims | |||
| Audit IPsec Extended Mode | |||
| Audit IPsec Main Mode | IF IF | ||
| Audit IPsec Quick Mode | |||
| Audit Logoff | Yes No | Yes No | Yes No |
| Audit Logon | Yes No | Yes Yes | Yes Yes |
| Audit Network Policy Server | Yes Yes | ||
| Audit Other Logon/Logoff Events | Yes Yes | ||
| Audit Special Logon (Configuring Special Logon Auditing) | Yes No | Yes No | Yes Yes |
| Object Access | |||
| Audit Application Generated | |||
| Audit Certification Services | |||
| Audit Detailed File Share | |||
| Audit File Share | |||
| Audit File System | |||
| Audit Filtering Platform Connection | |||
| Audit Filtering Platform Packet Drop | |||
| Audit Handle Manipulation | |||
| Audit Kernel Object | |||
| Audit Other Object Access Events | |||
| Audit Registry | |||
| Audit Removable Storage | |||
| Audit SAM | |||
| Audit Central Access Policy Staging | |||
| Policy Change | |||
| Audit Audit Policy Change | Yes No | Yes Yes | Yes Yes |
| Audit Authentication Policy Change | Yes No | Yes No | Yes Yes |
| Audit Authorization Policy Change | |||
| Audit Filtering Platform Policy Change | |||
| Audit MPSSVC Rule-Level Policy Change | Yes | ||
| Audit Other Policy Change Events | |||
| Privilege Use | |||
| Audit Non Sensitive Privilege Use | |||
| Audit Other Privilege Use Events | |||
| Audit Sensitive Privilege Use | |||
| System | |||
| Audit IPsec Driver | Yes Yes | Yes Yes | |
| Audit Other System Events | Yes Yes | ||
| Audit Security State Change | Yes No | Yes Yes | Yes Yes |
| Audit Security System Extension | Yes Yes | Yes Yes | |
| Audit System Integrity | Yes Yes | Yes Yes | Yes Yes |
| Global Object Access Auditing | |||
| Audit IPsec Driver | |||
| Audit Other System Events | |||
| Audit Security State Change | |||
| Audit Security System Extension | |||
| Audit System Integrity |
I set up my policy items the following way:
Account Logon
 |
| Figure 68. Account Logon Policy. |
Account Management
 |
| Figure 69. Account Management Policy. |
Detailed Tracking
 |
| Figure 70. Detailed Tracking Policy. |
DS Access
 |
| Figure 71. DS Access Policy. |
Logon/Logoff
 |
| Figure 72. Logon/Logoff Policy. |
Object Access
 |
| Figure 73. Object Access Policy. |
Policy Change
 |
| Figure 74. Policy Change Policy. |
Privilege Use
 |
| Figure 75. Privilege Use Policy. |
System
 |
| Figure 76. System Policy. |
Global Object Access
 |
| Figure 77. Global Object Access Policy. |
One last step ! Group Policy allows audit policy to be set only at the category level, and existing Group Policy settings may override the subcategory settings of new computers as they are joined to the domain or upgraded. Enabling the Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings policy settings allows audit policy to be managed by using subcategories without requiring a change to Group Policy. [Source]
 |
| Figure 78. Enabling Audit security option. |
Right click on the Security Option Policy item, click Properties, Enable it, and apply it.
 |
| Figure 79. Enabling Audit security option |
 |
| Figure 80. Enabling Audit security option |
 |
| Figure 81. Enabling Audit security option |
Link new "Full Domain Auditing Policy" GPO to the domain
Go back to your Group Policy Management Console, right click on your domain name and select "Link an Existing GPO".
 |
| Figure 82. Linking an existing GPO. |
Select your new GPO ("Full Domain Auditing Policy")
 |
| Figure 83. Linking an existing GPO. |
You will now see your new GPO under your root domain which means that it will be applied to your whole domain.
 |
| Figure 84. Linking an existing GPO. |
Make sure you force a user and computer policy update on your systems by executing gpupdate /force as shown in figure 85 below.
 |
| Figure 85. Updating user and computers policies. |
You have officially set up and configured your own domain at home. As I explained before, I highly encourage you to do more research and customize your own. Now, this is a good time to take a snapshot of your DC VM and your other Windows systems in your domain. Remember that if you make any major changes to your domain, make sure you create snapshots.
On the next post, I will show you how to set up our own hunting platform with the help of Elasticsearch, Logstash & Kibana (ELK).
Feedback is greatly appreciated! Thank you.




Pls correct figure 44. The command should be OU=Clients, OU=computers...
ReplyDeleteI got my already programmed and blanked ATM card to withdraw the maximum of $1,000 daily for a maximum of 20 days. I am so happy about this because i got mine last week and I have used it to get $20,000. Mike Fisher Hackers is giving out the card just to help the poor and needy though it is illegal but it is something nice and he is not like other scam pretending to have the blank ATM cards. And no one gets caught when using the card. get yours from Mike Fisher Hackers today! *email cyberhackingcompany@gmail.com
DeleteWhat has your government done to help save you from your financial instability? you strive to survive and yet you hear stories of how your leaders have become terror in your entities... is time to make a different. for will have made money, and we have also come to help you out from your long time of financial suffering. clearing of credit card is made available, software for hacking ATM machines, bank to bank hacking and transfer, change your school grade and become something useful in the society. we also have other form of services such as Facebook hack, whats-app hack, twitter hack, i cloud hack, tracking of smart phones, hacking CCTV, installation of software on desktop and PC, snap-chat hack, Skype hack, wire wire, bitcoin account hack, erase your criminal record and be free for ever. database hack and many more. e-mail: cyberhackingcompany@gmail.com for your genuine hacking services and we shock we your findings.
Delete**SSN FULLZ WITH HIGH CREDIT SCORES AVAILABLE**
Delete>For tax filling/return
>SSN dob DL all info included
>For SBA & PUA filling
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING CARDING CASHOUTS CLONING**
=>Contact 24/7<=
Telegram > @leadsupplier
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA AVAILABLE
SSN+DOB
SSN+DOB+DL
High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid info found, will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS AVAILABLE FOR
(Carding, spamming, hacking, scripting, scam page, Cash outs, dumps cash outs)
=>Ethical Hacking Tools & Tutorials
=>Kali linux
=>Facebook & Google hacking
=>Bitcoin Hacking
=>Bitcoin Flasher
=>SQL Injector
=>Bitcoin flasher
=>Viruses
=>Keylogger & Keystroke Logger
=>Logins Premium (Netflix, coinbase, FedEx, PayPal, Amazon, Banks etc)
=>Bulk SMS Sender
=>Bitcoin Cracker
=>SMTP Linux Root
=>DUMPS track 1 and 2 with & without pin
=>Smtp's, Safe Socks, rdp's, VPN, Viruses
=>Cpanel
=>PHP mailer
=>Server I.P's & Proxies
=>HQ Emails Combo (Gmail, yahoo, Hotmail, MSN, AOL, etc)
->Serious buyers are always welcome
->Big discount in bulk order
->Offer gives monthly, quarterly, half yearly & yearly
->Hope we do a great business together
CONTACT 24/7
Telegram > @leadsupplier
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
JOIN THE ILLUMINATI Whatsapp only +19174732351 OR info. smith666illuminati@gmail.com JOIN THE ILLUMINATI FROM USA, OR ANYWHERE AROUND THE WORLD TODAY BE RICH, FAME, AND POSSES POWER.email us on info. smith666illuminati@gmail.com OR call us on +19174732351
DeleteThis comment has been removed by a blog administrator.
ReplyDeleteBuy adderall
ReplyDeleteBuy Xanax
Buy Methamphetamine
Buy alprazolam powder
Buy oxycontin
Buy Ketamine
Thanks for sharing Active directory auditor tips. for more info i rfer cion systems Active directory auditor in USA.
ReplyDeleteThe Collection Marts is platform where you can view latest designs about home décor and bedding. We have large range in different categories with finest fabric in cotton and silk. You can view not only present trends but also view huge collection with reasonable price. heavy bed sheets , queen comforter sets , queen bed sheet sets , nishat linen bridal bed sheets , bedding sets uk , cotton razai , apricot sofa covers , velvet bed sheets , razai cover online , towel wholesale market in karachi The Collection Marts can provide fast service about delivery as well as customer support too. Our products are not only self-made but also, well connected with markets to ensure for possibility of available designs if client want to purchase. The Collection Marts customer support open 24/7 to guide their customers about material or product stuff.
ReplyDeleteapp v online training
ReplyDeletesccm online training
windows admin online training
mysql online training
vmware online training
tableau online training
This comment has been removed by the author.
ReplyDeleteI am really happy to read this blog post, you have many information put it on this article, am really suggest to my all dear friend to visit this blog post and collect this useful and valuable information. for More Information Click Here:- Install Epson Printer Driver without CD
ReplyDeleteSuch great information. I really appreciated your work and information. Thanks for sharing.
ReplyDeleteSurat is one of the best cities for tourism in India. It is also called Diamond Hub of the World. Surat is a popular tourist destination in Gujarat because of its historic romanticism and coastline graciousness. If you want to explore Places To Visit In Surat within your friendly budget, then please contact us, professionals.
**SSN FULLZ WITH HIGH CREDIT SCORES AVAILABLE**
ReplyDelete>For tax filling/return
>SSN dob DL all info included
>For SBA & PUA filling
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING CARDING CASHOUTS CLONING**
=>Contact 24/7<=
Telegram > @leadsupplier
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA AVAILABLE
SSN+DOB
SSN+DOB+DL
High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid info found, will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS AVAILABLE FOR
(Carding, spamming, hacking, scripting, scam page, Cash outs, dumps cash outs)
=>Ethical Hacking Tools & Tutorials
=>Kali linux
=>Facebook & Google hacking
=>Bitcoin Hacking
=>Bitcoin Flasher
=>SQL Injector
=>Bitcoin flasher
=>Viruses
=>Keylogger & Keystroke Logger
=>Logins Premium (Netflix, coinbase, FedEx, PayPal, Amazon, Banks etc)
=>Bulk SMS Sender
=>Bitcoin Cracker
=>SMTP Linux Root
=>DUMPS track 1 and 2 with & without pin
=>Smtp's, Safe Socks, rdp's, VPN, Viruses
=>Cpanel
=>PHP mailer
=>Server I.P's & Proxies
=>HQ Emails Combo (Gmail, yahoo, Hotmail, MSN, AOL, etc)
->Serious buyers are always welcome
->Big discount in bulk order
->Offer gives monthly, quarterly, half yearly & yearly
->Hope we do a great business together
CONTACT 24/7
Telegram > @leadsupplier
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
आपका लेख पढ़कर मुझे बहुत आनंद आया। यदि आप जन्म कुंडली के महत्त्व के विषय में और जानना चहाते हैं तो इस इसके लिए आप हमारी वेबसाइट पर दी गयी जानकारी पढ़ सकते हैं । अगर आप कुंडली मेकर के माध्यम से कुंडली बनवाना चहाते हैं तो आप यह भी कर सकते हैं।
ReplyDeleteJanam Kundli in Hindi
Kundli Matching for Marriage
How does Saturn in the 12th house affect natives
Do Horoscope Matching Really Work
What to do if horoscope do not match
Nakshatras compatibility for marriage
ReplyDeleteشركة صيانة افران
صيانة افران