One of the main reasons that encouraged me to start this series "Chronicles of a Threat Hunter" was the lack of detection techniques provided by security researchers after writing awesome pen-testing articles. Do NOT get me wrong, they do an EXCELLENT job describing tools and techniques used by real adversaries, but only a few share ways to detect or hunt for what they write about.
A few months ago, I read an article about moving laterally after compromising NT LAN Manager (NTLM) password hashes by leveraging PsExec-Style techniques. It was a great write-up, but It only provided information about the behavior of each tool at a high-level. You can read the article here.
In this post, I will show you what the attack looks like from a hunter's perspective. One thing that I found very interesting in the implementation of this technique was the execution of code (Stager) remotely via services right after authenticating to the box establishing a session with their command and control which is exactly what I will focus on in this post.
There are several ways to cause code to execute on a remote host. One of the most common methods is via the Windows Service Control Manager (SCM), which allows authorized users to remotely create and modify services. Several tools, such as PsExec, use this functionality. When a client remotely communicates with the Service Control Manager, there are two observable behaviors. First, the client connects to the RPC Endpoint Mapper over 135/tcp. This handles authentication, and tells the client what port the endpoint—in this case the SCM—is listening on. Then, the client connects directly to the listening port on services.exe. If the request is to start an existing service with a known command line, the the SCM process will run the corresponding command.[Source]
Requirements:
- Sysmon Installed (I have version 6 installed)
- Winlogbeat forwarding logs to an ELK Server
- I recommend to read my series "Setting up a Pentesting.. I mean, a Threat Hunting Lab" specifically part 5 & 6 to help you set up your environment if you haven't set up one yet.
- Success audit events for File Share and Detail File Share set up. I will show you how if you dont know how to update/edit an Audit Policy. .
- Metasploit's psexec Module
- Invoke-SMBExec.ps1 from the Invoke-TheHash project by Kevin Robertson
Remotely Launched Executables via Services
There are several ways to cause code to execute on a remote host. One of the most common methods is via the Windows Service Control Manager (SCM), which allows authorized users to remotely create and modify services. Several tools, such as PsExec, use this functionality. When a client remotely communicates with the Service Control Manager, there are two observable behaviors. First, the client connects to the RPC Endpoint Mapper over 135/tcp. This handles authentication, and tells the client what port the endpoint—in this case the SCM—is listening on. Then, the client connects directly to the listening port on services.exe. If the request is to start an existing service with a known command line, the the SCM process will run the corresponding command.[Source]
CreateService Function
Creates a service object and adds it to the specified service controls manager database. A few parameters that will help you understand a few codes used during this exercise are: [Source]
ServiceType
Value
|
Meaning
|
SERVICE_ADAPTER
0x00000004
|
Reserved.
|
SERVICE_FILE_SYSTEM_DRIVER
0x00000002
|
File system driver
service.
|
SERVICE_KERNEL_DRIVER
0x00000001
|
Driver service.
|
SERVICE_RECOGNIZER_DRIVER
0x00000008
|
Reserved.
|
SERVICE_WIN32_OWN_PROCESS
0x00000010
|
Service that runs in
its own process.
|
SERVICE_WIN32_SHARE_PROCESS
0x00000020
|
Service that shares
a process with one or more other services.
|
SERVICE_USER_OWN_PROCESS
0x00000050
|
The service runs in
its own process under the logged-on user account.
|
SERVICE_USER_SHARE_PROCESS
0x00000060
|
The service shares a
process with one or more other services that run under the logged-on user
account.
|
StartType
The service start options.
Value
|
Meaning
|
SERVICE_AUTO_START
0x00000002
|
A service started
automatically by the service control manager during system startup. For more
information, see Automatically Starting Services.
|
SERVICE_BOOT_START
0x00000000
|
A device driver
started by the system loader. This value is valid only for driver services.
|
SERVICE_DEMAND_START
0x00000003
|
A service started by
the service control manager when a process calls the StartService function.
|
SERVICE_DISABLED
0x00000004
|
A service that
cannot be started. Attempts to start the service result in the error
code ERROR_SERVICE_DISABLED.
|
SERVICE_SYSTEM_START
0x00000001
|
A device driver
started by the IoInitSystem function. This value is valid
only for driver services.
|
ErrorControl
The severity of the error, and action taken, if this service fails to start.
Value
|
Meaning
|
SERVICE_ERROR_CRITICAL
0x00000003
|
The startup program logs the error
in the event log, if possible. If the last-known-good configuration is being
started, the startup operation fails. Otherwise, the system is restarted with
the last-known good configuration.
|
SERVICE_ERROR_IGNORE
0x00000000
|
The startup program ignores the
error and continues the startup operation.
|
SERVICE_ERROR_NORMAL
0x00000001
|
The startup program logs the error
in the event log but continues the startup operation.
|
SERVICE_ERROR_SEVERE
0x00000002
|
The startup program logs the error
in the event log. If the last-known-good configuration is being started, the
startup operation continues. Otherwise, the system is restarted with the
last-known-good configuration.
|
CreateService Remarks
The CreateService function creates a service object and installs it in the service control manager database by creating a key with the same name as the service under the following registry key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
Information specified by CreateService, ChangeServiceConfig, and ChangeServiceConfig2 is saved as values under this key. The following are examples of values stored for a service.[Source]
Value
|
Description
|
DependOnGroup
|
Load-ordering groups
on which this service depends, as specified by lpDependencies.
|
DependOnService
|
Services on which this
service depends, as specified by lpDependencies.
|
Description
|
Description specified
by ChangeServiceConfig2 .
|
DisplayName
|
Display name specified
by lpDisplayName.
|
ErrorControl
|
Error control
specified by dwErrorControl.
|
FailureActions
|
Failure actions
specified by ChangeServiceConfig2 .
|
Group
|
Load ordering group
specified by lpLoadOrderGroup. Note that setting this value can
override the setting of the DependOnService value.
|
ImagePath
|
Name of binary file,
as specified by lpBinaryPathName.
|
ObjectName
|
Account name specified
by lpServiceStartName.
|
Start
|
When to start service,
as specified by dwStartType.
|
Tag
|
Tag identifier
specified by lpdwTagId.
|
Type
|
Service type specified
by dwServiceType.
|
Getting ready for the hunt
Getting a Sysmon Config ready
I will use use my basic sysmon config StartLogging.xml that helps me to filter out most of the noise on an initial Sysmon setup. You might have to add some more exclusions to it depending on how your Windows system is set up.
Download and save the Sysmon config in a preferred location of your choice. Then, update your Sysmon rules configuration. In order to do this, make sure you run cmd.exe as administrator, and update your Sysmon rules with the configuration you just downloaded by running the following commands:
Sysmon.exe -c [Sysmon config xml file]
Getting a Kibana dashboard ready
As you may already know about me, I prefer to look at all my logs in different visualizations under one dashboard in Kibana instead of using the event viewer console. It makes the analysis way easier allowing me to look at all the data at once and filter out noise. If you want to learn the basics of how to build a Kibana dashboard, you can read about it here and here. Create one similar to the one shown in figure 1 below.
 |
| Figure 1. Lateral Movement Dashboard. |
On the same dashboard, I like to also have a saved search of all the events sent to my ELK Server. You can just add it at the bottom of the visualizations shown in figure 1 above. That helps me to visualize my events in a timeline style as shown in figure 2 below.
 |
| Figure 2. TimeLine style for Lateral Movement dashboard. |
Update/Create an AD Global Audit Policy
For this exercise, we want to make sure that we have "File Share" audit events enabled. If you have a domain controller set up in your environment with AD services enabled, you can create Audit Policies and apply them to your whole domain. If you dont have a custom Audit Policy set up in your environment yet, you can follow one of my posts here starting on "Figure 59. Creating a new GPO" to help you create one. If you have one set up already, do the following:
- Open Group Policy Management > right-click on your custom Global Auditing Policy > Click on Edit
- It will open the Group Policy Management Editor
- Expand Computer Configuration> Windows Settings > Security Settings > Advanced Audit Policy Configuration> Audit Policies > ObjectAccess
- Once in ObjectAccess, right click on "Audit File Share" & "Audit Detailed File Share" and select "Configure the following audit events"
- Select the checkbox next to Success and Apply.
 |
| Figure 3. Enabling Audit File Share success events. |
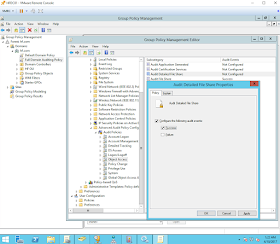 |
| Figure 4. Enabling Audit Detailed File Share success events. |
Finally, make sure you refresh local and Active Directory-based Group Policy settings on your endpoints. Run the following command on your endpoints as shown in figure 5 below:
gpupdate /force
 |
| Figure 5. Updating GPOs on endpoints. |
Delete/Clean your Index
If you have read my previous posts, you should know that in order to reduce the number of logs before and during executing an attack, make sure you delete/clear your Index by running the following command as shown below:
curl -XDELETE 'localhost:9200/[name of your index]?pretty'
Do this in your ELK server a few seconds before you run your tools against your compromised computer.
Hunting for Metasploit PsExec Module
Attack Scenario
An adversary dumped hashes from a compromised system's SAM database and used the Administrator's hash with the metasploit's psexec module to move laterally in the network.
Running Metasploit's PsExec module
Make sure you clear/delete your index before running the module.
 |
| Figure 6. Setting up PsExec Module options before executing it. |
 |
| Figure 7. Executing Metasploit's PsExec module. |
First look at our Dashboard
Go to your dashboard right away and refresh it to show you what happened in the past 15-30 minutes. I filtered EID 7 events to have a cleaner timeline of events and focus on authentication logs, registry events, process execution, etc.
 |
| Figure 8. Lateral Movement Dashboard First Look. |
I see a few interesting events:
- Win EID 4624
- Logon Type: 3 (Network)
- Package Name : NTLM V2
- Logon Process: NtLmSsp
- Key Length: 0
- Win 4672 Special Privileges assigned to new logon
- Win 4776 Credentials Validation
- Win 7045 A Service was installed in the system
- Sysmon EID 1 Images
- Services.exe
- PowerShell.exe
- Win EID 5140 & 5145 ShareNames
- \\*\IPC$
- \\*\ADMIN$
- Workstation communications
- P5MPJqc1EgXaOY1M ===> VA-WK-ACCT001.hf.com
- Kali machine: P5MPJqc1EgXaOY1M
- Target/Victim's Computer VA-WK-ACCT001.hf.com
- Sysmon EID 13 & 12 : Registry Keys (look in page 1 & 2)
- HKLM\System\CurrentControlSet\services\OzZkywlj
- HKLM\System\CurrentControlSet\services\OzZkywlj\Start
- HKLM\System\CurrentControlSet\services\OzZkywlj\DeleteFLag
- HKLM\System\CurrentControlSet\services\OzZkywlj\DisplayName
- HKLM\System\CurrentControlSet\services\OzZkywlj\ErrorControl
- HKLM\System\CurrentControlSet\services\OzZkywlj\ImagePath
- HKLM\System\CurrentControlSet\services\OzZkywlj\ObjectName
- HKLM\System\CurrentControlSet\services\OzZkywlj\Type
- Sysmon EID 13 & 12 Registry Events Details:
- DWORD (0x00000000,0x00000001,0x00000003,0x00000004,0x00000010)
- LocalSystem
- CFvsCYjeuYHYlewh
- Pipe Names
- \srvsvc
- \wkssvc
- <Anonymous Pipes>
- \ntsvcs
Events Timeline (I)
The first events are related to a successful authentication happening on the target machine and a new service being set up with specific properties.
 |
| Figure 9. First events. |
Authentication Events (Pass-The-Hash Activity)
EID 4776 (Attempt to validate the credentials for an account) - 04/10/17 19:15:36.169
When a system successfully authenticates a local SAM account via NTLM (instead of Kerberos), the system logs this event. This specifies which user account was used to log on and the computer's name from which the user initiated the logon in the Workstation Field as shown in figure 10 below.
 |
| Figure 10. Attempt to validate the credentials for an account. |
EID 4624 (An account was successfully logged on) - 04/10/17 19:15:36.169
An account successfully logged on from 172.18.39.101 (Kali) with an NTLM hash.
 |
| Figure 11. An account was successfully logged on. |
EID 4672 (Special privileges assigned to new logon) - 04/10/17 19:15:36.169
This event lets you know whenever an account assigned any "administrator equivalent" user rights logs on. For instance you will see event 4672 in close proximity to logon events (4624) for administrators since administrators have most of these admin-equivalent rights. [Source]. Remember that privileges such as SeTakeOwnership, SeDebug, and SeImpersonate are admin-equivalent.
File Share Activity (Is PowerShell installed?)
EID 5140 (A network share object was accessed) - 04/10/17 19:15:36.183
This log can tell us when a user accesses a network share, but it does not tell us the exact file that the user accessed in the share. So far, all I see is \??\C:\Windows.
 |
| Figure 12. A Network share object was accessed. |
EID 5145 (Detailed File Share event) - 04/10/17 19:15:36.190
Tracking the specific file that a user is accessing on a file share is possible when you have the Detailed File Share audit policy enabled. Now you understand why we enabled this audit policy at the beginning.
 |
| Figure 13. Checking PowerShell.exe via ADMIN$ |
Why check for PowerShell.exe?
As you can see in figure 14 below, the metasploit's PsExec module has a function to check for the presence of PowerShell in the target system. This is because the module has the option to use the old school way of dropping an executable onto the victim if PowerShell is not installed.
 |
| Figure 14. PsExec module checking if PowerShell is installed or not in the victim's system. |
Service Control Manager (SCM) Access
EID 18 - 04/10/17 19:15:36.237
During system startup, a named pipe NTSVCS is created as a remote procedure call (RPC) interface between the SCM and the SCPs (Service Control Processes) that interact with specific services. This event 18 is logged when a connection to a pipe is established. Common behavior when a service is about to be installed, created or modified.
 |
| Figure 15. \ntsvcs pipe connected. |
EID 4674 (An operation was attempted on a privileged object) - 04/10/17 19:15:36.279
This specific event is also known for when a service is about to get installed, started, stopped or modified. We can see that the account used for this is the compromised account used to pass the hash.
 |
| Figure 16. Access to SC Manager Object. |
Service Creation and Installation
EID 12 (Registry object added or deleted) - 04/10/17 19:15:36.352
In this specific event, a Key was created with a random name.
 |
| Figure 17. Creating a random key for the new service. |
EID 13 ( Registry Value Set) - 04/10/17 19:15:36.353 - 04/10/17 19:15:36.354
As you could see in figure 9 above, a new service was set up with specific values. One of the values that stand out is the value set to the ImagePath property of the new service as shown in figure 18 below.
- HKLM\System\CurrentControlSet\services\OzZkywlj\ErrorControl
- Details: DWORD (0x00000000)
- Value: SERVICE_ERROR_IGNORE
- HKLM\System\CurrentControlSet\services\OzZkywlj\Start
- Details: DWORD (0x00000003)
- Value: SERVICE_DEMAND_START
- HKLM\System\CurrentControlSet\services\OzZkywlj\Type
- Details: DWORD (0x00000010)
- Value: SERVICE_WIN32_OWN_PROCESS
- HKLM\System\CurrentControlSet\services\OzZkywlj\ImagePath
- Details: %%COMSPEC%% /b /c start /b /min powershell.exe -nop [Truncated]
- HKLM\System\CurrentControlSet\services\OzZkywlj\DisplayName
- Details: CFvsCYJeuYHYlewh
- HKLM\System\CurrentControlSet\services\OzZkywlj\ObjectName
- Details: LocalSystem
 |
| Figure 18. Metasploit Stager set up as part of the ImagePath property of the new service. |
EID 7045 (A service was installed in the system) - 04/10/17 19:15:36.354
A System log that also provides information about a new service installed in the endpoint. This is also captured by EID 4697 if configured or enabled by default.
 |
| Figure 19. A service was installed in the system. |
Events Timeline (II)
Once the service is installed, it is executed and a connection is established with the Metasploit Server. Then, the registry key holding the new service is deleted.
 |
| Figure 20. Timeline of initial events. Part II. |
Execution of New Service
EID 1 (Process Create) - 04/10/17 19:15:36.382 - 04/10/17 19:15:36.411
Once the service gets started, services.exe runs the code or script set up under the IpagePath property of the new service. In this case, services as a parent runs cmd.exe (%%COMSPEC%%) to execute the rest of the commands/script (Stager)
 |
| Figure 21. Services executing the script |
Powershell gets spawned by cmd.exe and the rest of the code gets executed to finally establish the connection back with the Metasploit server. As you can see in figure 22 below, the Integrity level of the process is SYSTEM due to the fact that services get started/executed with SYSTEM privileges.
 |
| Figure 22. Stager being executed by PowerShell. |
Deletion of Reg Key (New Service)
EID 13 (Registry Value Set) - 04/10/17 19:15:36.419
After executing the new service and running the metasploit stager from the ImagePath property of the service, the service is disabled and set to be deleted.
- HKLM\System\CurrentControlSet\services\OzZkywlj\Start
- Details: DWORD (0x00000004)
- Value: SERVICE_DISABLED
- HKLM\System\CurrentControlSet\services\OzZkywlj\DeleteFlag
- Details: DWORD (0x00000001)
- Value: DELETE
 |
| Figure 23. Setting a DeleteFlag to the new service. |
EID 12 (Registry object added or deleted) - 04/10/17 19:15:36.440
After the DeleteFlag is set, the registry key is deleted by services.exe.
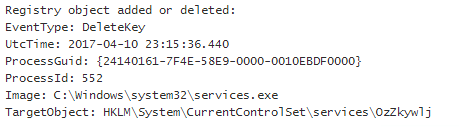 |
| Figure 24. Deleting Service. |
Summary of Chains of Events Observed
Time Bucket: All within 1 second. Events ordered following their respective timestamps.
Source
|
EventID
|
Field
|
Details
|
WinEvent
|
4776
|
PackageName
|
MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
|
WinEvent
|
4776
|
Logon Account/TargetUserName
|
Administrator
|
WinEvent
|
4624
|
Source Workstation/WorkstationName
|
P5MPJqc1EgXaOY1M
|
WinEvent
|
4624
|
LogonType
|
3
|
WinEvent
|
4624
|
WorkstationName
|
P5MPJqc1EgXaOY1M
|
WinEvent
|
4624
|
Source Network Address/IPAddress
|
NOT (::1 OR Localhost)
|
WinEvent
|
4624
|
LogonProcessName
|
NtLmSsp
|
WinEvent
|
4624
|
LmPackageName
|
NTLM V2
|
WinEvent
|
4624
|
KeyLength
|
0
|
WinEvent
|
4672
|
SubjectUsername/ TargetUserName
|
Administrator
|
WinEvent
|
5140
|
SubjectUsername
|
Administrator
|
WinEvent
|
5140
|
ShareName
|
\\*\ADMIN$ OR \\*\C$
|
WinEvent
|
5140
|
Source Address/IPAddress
|
172.18.39.101
|
WinEvent
|
5145
|
RelativeTargetName
|
System32\WindowsPowerShell\v1.0\powershell.exe
OR Windows\System32\WindowsPowerShell\v1.0\powershell.exe
|
WinEvent
|
5145
|
SubjectUsername
|
Administrator
|
WinEvent
|
5145
|
ShareName
|
\\*\ADMIN$ OR \\*\C$
|
WinEvent
|
5145
|
Source Address/IPAddress
|
172.18.39.101
|
Sysmon
|
18
|
PipeName
|
\ntsvcs
|
WinEvent
|
4674
|
ObjectServer
|
SC Manager
|
WinEvent
|
4674
|
ObjectType
|
SC_MANAGER OBJECT
|
WinEvent
|
4674
|
SubjectUsername
|
Administrator
|
Sysmon
|
12
|
EventType
|
CreateKey
|
Sysmon
|
12
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
12
|
TargetObject
|
HKLM\System\CurrentControlSet\services\OzZkywlj
|
Sysmon
|
13
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
13
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\OzZkywlj"
AND (ErrorControl OR Start OR Type OR DisplayName OR ObjectName)
|
Sysmon
|
13
|
Details
|
("DWORD" AND (0x00000000
OR 0x00000003 OR 0x00000010)) AND CFvsCYJeuYHYlewh OR LocalSystem
|
Sysmon
|
13
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\OzZkywlj\ImagePath"
|
Sysmon
|
13
|
Details
|
%%COMSPEC%% OR cmd.exe OR
powershell.exe OR Long Strings.
|
WinEvent
|
7045/4697
|
Service Name
|
CFvsCYJeuYHYlewh
|
WinEvent
|
7045/4607
|
Service File Name
|
%%COMSPEC%% OR cmd.exe OR
powershell.exe OR Long Strings.
|
Sysmon
|
1
|
ParentImage
|
C:\Windows\system32\services.exe
|
Sysmon
|
1
|
Image
|
cmd.exe OR powershell.exe
|
Sysmon
|
13
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
13
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\OzZkywlj\"
AND (Start OR DeleteFlag)
|
Sysmon
|
13
|
Details
|
"DWORD" AND (0x00000004
OR 0x00000001)
|
Sysmon
|
12
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
12
|
EventType
|
DeleteKey
|
Sysmon
|
12
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\OzZkywlj"
|
RT: "Great, all I have to do is use another tool for lateral movement!"
I hear that all the time, and believe me, we (hunters) also have common sense :) and think about you using another tool, renaming processes or running things in memory. I am not trying to come up with a signature for an specific tool; Instead, I am trying to focus on the patterns of behavior of this technique used to move laterally. Let's say you want to use Invoke-SMBExec.ps1 from the Invoke-TheHash project by Kevin Robertson. What does it look like?
Hunting for Invoke-SMBExec (Invoke-TheHash)
Running Invoke-SMBExec
Make sure you clear/delete your index before running the module.
Let's take a look at our Dashboard
Go to your dashboard, and refresh it to show you what happened in the past 15-30 minutes. I filtered EID 7 to not look at the images loaded on the systems allowing me to have a cleaner timeline of events and focus on authentication logs, registry events, etc.
Doesn't it look familiar?
Doesn't it look familiar?
 |
| Figure 27. Looking at Invoke-SMBExec activity. |
A few events
EID 4624 - (Pass The hash activity) - 04/11/17 - 01:22:37.725
 |
| Figure 28. Pass The hash log. |
EID 13 - (ImagePath Property) - 04/11/17 - 05:22:38.322
| Figure 29. Creation of malicious service. Set to execute Empire Stager. |
EID 7045 (Service Installed on System) - 04/11/17 - 01:22:38.322
| Figure 30. New Service Installed |
EID 1 (Execution of Stager by Services.exe) - 04/11/17 - 05:22:38.483
 |
| Figure 31. Execution of Stager. |
 |
| Figure 32. Execution of Stager |
EID 12 (Deletion of Registry key/New Service) - 04/11/17 - 05:23:08.677
 |
| Figure 33. Deletion of registry key. |
Summary of Chains of Events Observed (Pattern Approach)
Time Bucket: All within 1-2 seconds
Source
|
EventID
|
Field
|
Details
|
WinEvent
|
4624
|
PackageName
|
MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
|
WinEvent
|
4624/4672
|
Logon Account/TargetUserName
|
Administrator
|
WinEvent
|
4624
|
Source Workstation/WorkstationName
|
Other Workstations
|
WinEvent
|
4624
|
LogonType
|
3
|
WinEvent
|
4624
|
WorkstationName
|
Other Workstations
|
WinEvent
|
4624
|
Source Network Address/IPAddress
|
NOT (::1 OR Localhost)
|
WinEvent
|
4624
|
LogonProcessName
|
NtLmSsp
|
WinEvent
|
4624
|
LmPackageName
|
NTLM V2
|
WinEvent
|
4624
|
KeyLength
|
0
|
WinEvent
|
5140
|
SubjectUsername
|
NOT a ComputerName$
|
WinEvent
|
5140
|
ShareName
|
\\*\IPC$ OR \\*\ADMIN$ OR \\*\C$
|
WinEvent
|
5140
|
Source Address/IPAddress
|
NOT ( ::1 OR Localhost)
|
WinEvent
|
5145
|
RelativeTargetName
|
svcctl OR .exe OR Outlier
|
WinEvent
|
5145
|
SubjectUsername
|
NOT a ComputerName$
|
WinEvent
|
5145
|
ShareName
|
\\*\IPC$ OR \\*\ADMIN$ OR \\*\C$
|
WinEvent
|
5145
|
Source Address/IPAddress
|
NOT ( ::1 OR Localhost)
|
Sysmon
|
18
|
PipeName
|
\ntsvcs
|
Sysmon
|
12
|
EventType
|
CreateKey
|
Sysmon
|
12
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
12
|
TargetObject
|
HKLM\System\CurrentControlSet\services\[New Service]
|
Sysmon
|
13
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
13
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\" AND
(ErrorControl OR Start OR Type OR DisplayName OR ObjectName)
|
Sysmon
|
13
|
Details
|
("DWORD" AND (0x00000000 OR 0x00000003 OR 0x00000010)) OR Random Service Name OR LocalSystem
|
Sysmon
|
13
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\" AND
"ImagePath"
|
Sysmon
|
13
|
Details
|
%%COMSPEC%% OR cmd.exe OR powershell.exe OR Long Strings.
|
WinEvent
|
7045/4697
|
Service Name
|
Suspicious Name / Random
|
WinEvent
|
7045/4697
|
Service File Name
|
%%COMSPEC%% OR cmd.exe OR powershell.exe OR Long Strings.
|
Sysmon
|
1
|
ParentImage
|
C:\Windows\system32\services.exe
|
Sysmon
|
1
|
Image
|
cmd.exe OR powershell.exe
|
Sysmon
|
13
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
13
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\" AND (Start
OR DeleteFlag)
|
Sysmon
|
13
|
Details
|
"DWORD" AND (0x00000004 OR 0x00000001)
|
Sysmon
|
12
|
Image
|
C:\Windows\system32\services.exe
|
Sysmon
|
12
|
EventType
|
DeleteKey
|
Sysmon
|
12
|
TargetObject
|
"HKLM\System\CurrentControlSet\services\[Random Name]"
|
Final Thoughts
It was a very interesting exercise to go deeper into the functionality of the two tools I tested in this post, and it was even more interesting to capture their patterns of behaviors when remotely executing code via services to move laterally.
We could use the the chains of events observed on both scenarios and come up with a pattern that could allow us to reduce the number of false positives when hunting for this specific lateral movement technique.
We could create a basic logic with a few events:
EID 4624 + (EID 13 AND ("HKLM\System\CurrentControlSet\services\" AND "ImagePath" AND Details: (Long strings OR Base64 OR Suspicious Commands)) + (EID 7045/4697 AND ServiceFileName:(Long strings OR Base64 OR Suspicious Commands)) + (EID 1 AND ParentImage:services.exe AND CommandLine:(Long strings OR Base64 OR Suspicious Commands)) + (EID 12 AND EventType:"DeleteKey" AND TargetObject:""HKLM\System\CurrentControlSet\services\ [RandomName]") within a bucket time of 1-2 seconds.
A quick WIN?
I got you, why dont you look for the following?
event_id:13 AND Image:services.exe AND TargetObject: ("HKLM\\System\\CurrentControlSet\\services\\" AND "ImagePath" ) AND Details: /.{50,}/
that should give you long strings (unusual behavior) being set as values of ImagePath parameters of new or current services. That should annoy your RT :) (CobalStrike, Metasploit, Invoke-SMBExec, and potentially other tools leveraging this technique)
Hunting Techniques recommended
"Grouping consists of taking a set of multiple unique artifacts and identifying when multiple of them appear together based on certain criteria. The major difference between grouping and clustering is that in grouping your input is an explicit set of items that are each already of interest. Discovered groups within these items of interest may potentially represent a tool or a TTP that an attacker might be using. An important aspect of using this technique consists of determining the specific criteria used to group the items, such as events having occurred during a specific time window.This technique works best when you are hunting for multiple, related instances of unique artifacts, such as the case of isolating specific reconnaissance commands that were executed within a specific timeframe."
Searching [Source]
The simplest method of hunting, searching is querying data for specific artifacts and can be performed in most tools. Unfortunately it may not always be the most effective method because it cannot produce outliers in the result set; you get exactly the results you searched for.Searching also requires a finely defined search criteria to prevent result overload. A search that is too broad will often flood an analyst with too many results to realistically process.
The ThreatHunter-Playbook
I have started to post all my findings into A ThreatHunter-Playbook. I started this project with other hunters in the industry to share knowledge and aid the development of techniques and hypothesis for hunting campaigns.
Project Github Link: https://github.com/Cyb3rWard0g/ThreatHunter-Playbook
Join the team and share what works for you!
Feedback is greatly appreciated! Thank you.


