Requirements
Tools
Getting Started with Sysmon
Sysmon Overview
Sysmon is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. In contrast to common Antivirus/HIDS solutions, Sysmon performs system activity deep monitoring, and log high-confidence indicators of advanced attacks. Sysmon is using a device driver and a service that is running in the background and loads very early in the boot process. [Source]
Sysmon Tags and Events
ID
|
Tag
|
Event
|
1
|
ProcessCreate
|
Process Create
|
2
|
FileCreateTime
|
File creation
time
|
3
|
NetworkConnect
|
Network
connection detected
|
4
|
n/a
|
Sysmon service
state change (cannot be filtered)
|
5
|
ProcessTerminate
|
Process
terminated
|
6
|
DriverLoad
|
Driver Loaded
|
7
|
ImageLoad
|
Image loaded
|
8
|
CreateRemoteThread
|
CreateRemoteThread
detected
|
9
|
RawAccessRead
|
RawAccessRead
detected
|
10
|
ProcessAccess
|
Process
accessed
|
11
|
FileCreate
|
File created
|
12
|
RegistryEvent
|
Registry object
added or deleted
|
13
|
RegistryEvent
|
Registry value
set
|
14
|
RegistryEvent
|
Registry object
renamed
|
15
|
FileCreateStreamHash
|
File stream
created
|
16
|
n/a
|
Sysmon
configuration change (cannot be filtered)
|
17
|
PipeEvent
|
Named pipe
created
|
18
|
PipeEvent
|
Named pipe
connected
|
Sysmon XML Conditions
Condition
|
Description
|
Is |
Default, values
are equals
|
is not
|
Values are
different
|
Contains
|
The field
contains this value
|
Excludes
|
The field does
not contain this value
|
begin with
|
The field
begins with this value
|
end with
|
The field ends
with this value
|
less than
|
Lexicographical
comparison is less than zero
|
more than
|
Lexicographical
comparison is more than zero
|
Image
|
Match an image
path (full path or only image name). For example: lsass.exe will match
c:\windows\system32\lsass.exe
|
Great Sysmon Use Cases
- BotConf2016 Advanced Incident Detection and Threat Hunting using Sysmon (and Splunk) Tom Ueltschi 2016 (Slides)
- BotConf2016 Advanced Incident Detection and Threat Hunting using Sysmon (and Splunk) Tom Ueltschi 2016 (Video)
- Microsoft Sysmon Deployment 2017 - Dimitris Margaritis (slides)
- Splunkmon - Takin Sysmon to the Next Level (Whitepaper)
- Posh-Sysmon Module for Creating Sysmon Configuration Files 2017(Article)
- How to Go from Responding to Hunting with Sysinternals Sysmon RSAC 2017 (Slides)
- Hunting with Sysmon - Michael Haag 2017 (Article)
- Sysmon-dfir - Michael Haggis (Github)
- Sysinternals Sysmon unleashed (Article)
- SwiftOnSecurity - Sysmon Config 2017 (Github)
- Explaining and adapting Tay's Sysmon Configuration (Article)
Installing Sysmon
I had already installed Sysmon V5 in my systems, but with a recent update from Mark Russinovich, I needed to update a few images, and content in this post.
 |
| Figure 1. Sysmon V6 FYI release. |
To get started download Sysmon V6 from here.
 |
| Figure 2. Sysmon V6 Download page. |
Extract contents of the zipped file to a preferred directory.
 |
| Figure 3. Extracting files to tools directory. |
Launch cmd.exe as administrator, navigate to the folder where sysmon was extracted to, and if you want to know what sysmon can do just type:
sysmon.exe /?
 |
| Figure 4. Sysmon Menu. |
We can go ahead and try a basic installation by running the following command:
sysmon.exe -i -accepteula -h md5,sha256,imphash -l -n
- - i : Install Service and driver. Optionally take a configuration file.
- -h : Specify the hash algorithms used for image identifications
- -l : Log loading of modules. Optionally take a list of processes to track
- -n : Log network connections
 |
| Figure 5. Installing Sysmon. |
Now, if we run Eventviewer as administrator and browse to Applications and Services Logs > Microsoft > Windows > Sysmon > Operational, you will see that Sysmon is already working and generating logs as shown in figure 6 below.
 |
| Figure 6. Sysmon Logs. |
You can also view the configuration which Sysmon is running on by typing:
sysmon.exe -c
 |
| Figure 7. Current Configuration. |
How do we update our current configuration and apply rules to it?
sysmon.exe -c Your_custom_config.xml
You can use my StartLogging.xml config as a basic first script to start. This script has several Event IDs set to Log everything, and this is because I want you to tune it your way.. I just had a few exclusions already set there specially for Event IDs 1, 3, 6, 7, 10, 11, 12,13,14 to help you a little bit with filtering some initial noise.
Lets update our current config and apply our StartLogging.xml configuration.
 |
| Figure 8. Updating current configuration and showing it on console. |
You will not see many logs being generated, but that will change as soon as you start testing a few things. We have not set up our winlogbeat data shipper, but I will highly recommend to turn winlogbeat services off until you tune your sysmon configuration so that it captures the main anomalies from the attack you are executing. Once you are comfortable with your sysmon config, turn on your winlogbeat service and you will be able to see the events in your Kibana dashboard.
This can be a good time to take a snapshot on your endpoints with Sysmon installed.
Getting started with Winlogbeat
Stay in the windows computer where you set up Sysmon. To get started, download Winlogbeat from here and copy the unzipped folder to C:\Program Files\ as indicated by the Getting Started Winlogbeat Guide.
 |
| Figure 9. Winlogbeat Download page. |
 |
| Figure 10. Save the zipped file to your drive. |
 |
| Figure 11. Winlogbeat folder unzipped. |
 |
| Figure 12. Copying winlogbeat folder to indicated location. |
 |
| Figure 13. Winlogbeat folder copied to C:\Program Files\ . |
Open PowerShell as administrator, navigate to the winlogbeat folder contents and run the install-winlogbeat-service.ps1 powershell script.
.\install-winlogbeat-service.ps1
 |
| Figure 14. Run PowerShell as administrator. |
 |
| Figure 15. Navigate to your winlogbeats folder. |
 |
| Figure 16. Running install-service-winlogbeat.ps1 script. Also, using Run Once option. |
Next, run notepad as administrator. This will allow us to edit the winlogbeat config file and saving it without having "access denied" warning messages. Once notepad is open, open the winlogbeat.yml file in your winlogbeat folder.
 |
| Figure 17. Opening notepad as administrator. |
 |
| Figure 18. Opening winlogbeat.yml file in notepad. |
You will now be able to edit what log types it collects. We will add the following line after - name: System
Add: - name: Microsoft-windows-sysmon/operational
 |
| Figure 19. Original first part of the winlogbeat config. |
 |
| Figure 20. Adding Sysmon Logs to the configuration. |
Next, you can see that elasticsearch by default is configured to be the output to use when sending the data collected by the beat. We are going to change that by doing the following:
Add a # sign before Output.elasticsearch (as shown in figure 22)
Add a # sign before hosts: ["localhost:9200"] (as shown in figure 22 below)
 |
| Figure 21. Original Elasticsearch output configuration. |
 |
| Figure 22. Adding # signs to the Elasticsearch output section to disable the output. |
Now, it is time to configure the Logstash Output of the winlogbeat configuration. As you can see, we can set up the certificate that we created in our Ubuntu server in our previous post. We are going to make some changes to this part, but first make sure you have your cert created as shown in figure 24 below. If you did not create the certificate and private key in the previous host, I recommend to go back to it and do it before we continue.
 |
| Figure 23. Original Logstash Output section. |
 |
| Figure 24. Making sure cert exists in our ELK server. |
Use PSCP.exe to retrieve the certificate from the ELK server. Make sure SSH services are running in your ELK server before doing this. You can download PSCP.exe as part of a Putty bundle from here.
 |
| Figure 25. PSCP.exe to retrieve certificate from ELK server via SSH. |
Once you are ready run the following:
.\PSCP.EXE <username>@<IP of you ELK>:/etc/pki/tls/certs/logstash-forwarder.crt C:\<anywhere in your windows system>
 |
| Figure 26. Copying certificate from ELK to your Windows computer. |
 |
| Figure 27. Certificate was copied successfully. |
Now, back in our Logstash output section, do the following:
- Delete the # signs from Output.logstash (as shown in figure 28)
- Delete the # signs from hosts: ["Your ELK IP address:5044"] (as shown in figure 28)
- Delete the # signs from ssl.certificate_authorities: ['C:\<wherever you copied your cert to'] (as shown in figure 28)
 |
| Figure 28. Logstash configured to be the default output. |
Test your winlogbeat config by running:
.\winlogbeat.exe -c .\winlogbeat.yml -configtest -e
 |
| Figure 29. Config OK. |
Finally, you will have to start the winlogbeat service. You can use your PowerShell to do it by typing:
start-service winlogbeat
 |
| Figure 30. Starting the winlogbeat service. |
 |
| Figure 31. Starting the winlogbeat service. |
 |
| Figure 32. The winlogbeat service started successfully. . |
Next, open your favorite browser and go to your ELK's IP address. You will be able to substitute logstatsh-* for winlogbeat-* and set the field name to Timestamp as shown in figure 33 below. Click on the create option at the bottom to continue.
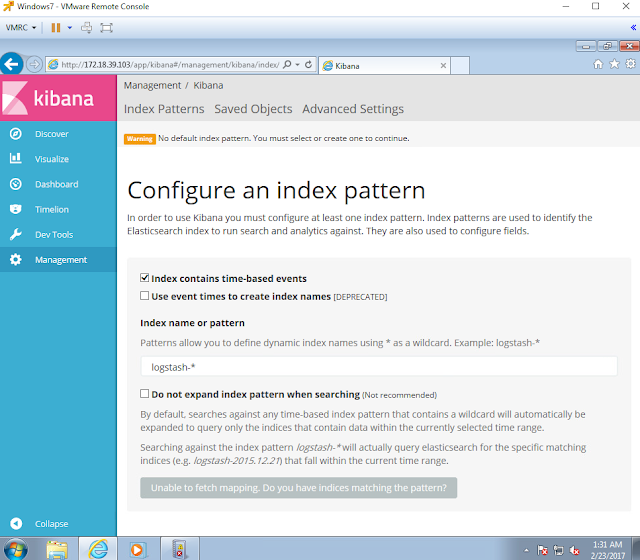 |
| Figure 33. Index Pattern configuration. |
 |
| Figure 34. Index Pattern configuration. |
You will be prompt to see how your winlogbeat-* index is storing the logs hitting your ELK. Next, on the left panel options, click on Discover to look at your logs.
 |
| Figure 35. Winlogbeat index. |
 |
| Figure 36. Searching for logs. |
 |
| Figure 37. Logs made it to our ELK stack. |
Below your Winlogbeat-* index, you can actually hover the data fields and click on the option add. You will be able to add as many fields as you want making it easier to read the logs.
 |
| Figure 38. Adding fields to our discover view. |
WOW! We made it! We have officially finished setting up our basic threat hunting lab. Remember, this is just the beginning. There are so many things that you can add to this lab setup, but I will leave that to your imagination and your own research.
Now, the one million dollar question,
HOW DO I USE ALL THIS TO START TRAINING MY HUNTING SKILLS?
I will give you a sneak peek of what I will do in my next series "Chronicles of a Threat Hunter" with a basic example:
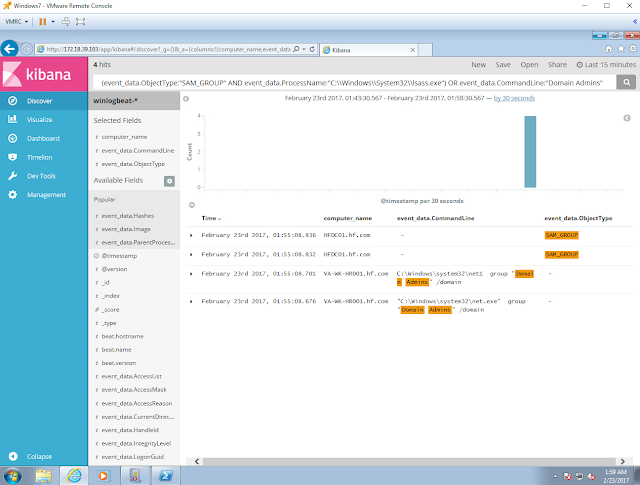
Hunting for users in the network interrogating AD to know who the Domain Admins are
 |
| Figure 39. Net.exe interrogating our AD for Domain Admin users. |
Query:
(event_data.ObjectType:"SAM_GROUP" AND event_data:ProcessName:"C:\\Windows\\System32\\lsass.exe") OR event_data.CommandLine:"Domain Admins"
 |
| Figure 40. Hunting for the HUNTER :) . |
That's it, and I hope you found this series helpful to start setting up your own lab. Let me know how this works out for you. #SharingIsCaring
LET THE HUNT BEGIN!
Feedback is greatly appreciated! Thank you.
Thanks a ton for this awesome post.
ReplyDeletePlease fix:
start-server winlogbeat => start-service winlogbeat
Although i had few problems initially mostly due to connectivity between the windows and ubuntu vm. Firewall on ubuntu was blocking connection from windows vm :).
Still i am facing an issue where using the certificates for ssl connection prevents sending winevents back to logstash (ubuntu vm).
But finally got it all setup without ssl part in the configuration as of now.
Based on a hint from this reference:
https://discuss.elastic.co/t/winlogbeat-issues-shipping-to-logstash/50557
output.logstash:
# The Logstash hosts
hosts: ["192.168.1.6:5044"]
# Optional SSL. By default is off.
# List of root certificates for HTTPS server verifications
#ssl.certificate_authorities: ['C:\elk\certs\logstash-forwarder.crt']
Quite a fun !!
Thanks again.
Hey sessionpool, Thank you for the feedback. I wonder if there is something missing from the Logstash configuration from https://cyberwardog.blogspot.com/2017/02/setting-up-pentesting-i-mean-threat_98.html starting from Figure 37. Specially in figures 40 & 41. Make sure the SubjectAltName is set up and pointing to your Host's IP before you create your certificate. Let me know if this helps. Thank you again for your feedback and glad you are having fun with these tutorials :)
DeleteI got my already programmed and blanked ATM card to withdraw the maximum of $1,000 daily for a maximum of 20 days. I am so happy about this because i got mine last week and I have used it to get $20,000. Mike Fisher Hackers is giving out the card just to help the poor and needy though it is illegal but it is something nice and he is not like other scam pretending to have the blank ATM cards. And no one gets caught when using the card. get yours from Mike Fisher Hackers today! *email cyberhackingcompany@gmail.com
DeleteI was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting (officialhackingcompany@gmail.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with$50,000,000.00 so i requested for one & paid the delivery fee to obtain the card, after 24 hours later, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich.Email: officialhackingcompany@gmail.com website: https://official-hacking-company.jimdosite.com/
DeleteWhat has your government done to help save you from your financial instability? you strive to survive and yet you hear stories of how your leaders have become terror in your entities... is time to make a different. for will have made money, and we have also come to help you out from your long time of financial suffering. clearing of credit card is made available, software for hacking ATM machines, bank to bank hacking and transfer, change your school grade and become something useful in the society. we also have other form of services such as Facebook hack, whats-app hack, twitter hack, i cloud hack, tracking of smart phones, hacking CCTV, installation of software on desktop and PC, snap-chat hack, Skype hack, wire wire, bitcoin account hack, erase your criminal record and be free for ever. database hack and many more. e-mail: cyberhackingcompany@gmail.com for your genuine hacking services and we shock we your findings.
Delete**SSN FULLZ WITH HIGH CREDIT SCORES AVAILABLE**
Delete>For tax filling/return
>SSN dob DL all info included
>For SBA & PUA filling
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING CARDING CASHOUTS CLONING**
=>Contact 24/7<=
Telegram > @killhacks
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA AVAILABLE
SSN+DOB
SSN+DOB+DL
High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid info found, will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS AVAILABLE FOR
(Carding, spamming, hacking, scripting, scam page, Cash outs, dumps cash outs)
Ethical Hacking Tools & Tutorials
Kali linux
Facebook & Google hacking
Bitcoin Hacking
Bitcoin Flasher
SQL Injector
Bitcoin flasher
Viruses
Keylogger & Keystroke Logger
Logins Premium (Netflix, coinbase, FedEx, PayPal, Amazon, Banks etc)
Bulk SMS Sender
Bitcoin Cracker
SMTP Linux Root
DUMPS track 1 and 2 with & without pin
Smtp's, Safe Socks, rdp's, VPN, Viruses
Cpanel
PHP mailer
Server I.P's & Proxies
HQ Emails Combo (Gmail, yahoo, Hotmail, MSN, AOL, etc)
->Serious buyers are always welcome
->Big discount in bulk order
->Offer gives monthly, quarterly, half yearly & yearly
->Hope we do a great business together
CONTACT 24/7
Telegram > @killhacks
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
there's some typo in the query field. i think should be:
ReplyDelete(event_data.ObjectType:"SAM_GROUP" AND event_data.ProcessName:"C:\\Windows\\Sytem32\\lsass.exe") OR event_data.CommandLine:"Domain Admins"
BTW, very good tutorials and step by step configuration. Thank you a lot!
Hey teedeearr, thank you for the observation. Fixing it now. I think it was really late when I typed that query :) . I am glad to hear you found the tutorials very helpful :)
DeleteThanks for this Wardog, any idea how you can deploy sysmon on +3K workstations ? Without downtown ?
ReplyDeleteThanks for the great writeup! Why would you exclude Lsass from ProcessAccess? Also is there a parameter option that i could pass to Sysmon to enable ProcessAccess instead of a config file? Thanks.
ReplyDeleteHey Abdulellah, I am excluding Lsass from ProcessAccess but as a the source and not the target. There are several processes that Lsass usually interacts with and causes several FPs. I was just excluding the processes that were very noisy as "source". I like to monitor lsass as a target for any suspicious access from a suspicious process. I can enable lsass as a source in the config but it will not tell me much. I feel that lsass as a target could tell me more and would be more interesting to investigate (just my opinion). Regarding enabling ProcessAccess w/o a config file, I dont think it is possible. The only arguments accepted via the sysmon binary are just to enable modules being loaded, hashing, and network events. The rest needs to be specified via a config file. I hope this helps.
DeleteHello Wardog. Thanks for the fantastic write up. I set up the environment flawlessly. Looking forward to more of your content. It's the best I've found on log analysis with elasticstack, period. How can I stay breast of your future projects? Thanks.
ReplyDeleteHey Z3nyth! sorry for the late response, I really appreciate the feedback and I am glad that you were able to install your environment without a problem :) :) I am in the process of adding more things to the HELK build and you can check all the updates by following me in Github or twitter:
DeleteGithub: https://github.com/Cyb3rWard0g
Twitter: @Cyb3rWard0g
I hope you have a great weekend!
Hi, I followed everything step by step however I am stuck on figure 33/34... First of all, I don't have an option to tick "Index contains time-based events" - this does not exist. Secondly, nothing is happening when I type Winlogbeat-*. I still unable to fetch mapping and cannot select any Time Filter field name. I am not sure what is going on as I followed everything step by step and everything up to figure 33 is working fine exactly as described in your tutorial. Any ideas please?
ReplyDeleteHey Nleocenlony! mhhhmmm what version are you running and is you endpoint sending logs to your ELK? it seems that you have the ELK ready to receive logs but not creating the winlogbeat-* index. Have you check if your endpoint is sending data?? can you disable the local firewall?? try to ping the ELK ip and see if you get a response. Also, what I would do is check your logstash logs : tail -f /var/log/logstash/logs* and see if there is anything stopping you from getting logs. Let me know what happens after checking all that. Happy to help !
DeleteThanks for the reply. I am not sure how I've done it but I finally managed to create winlogbeat-* index. Logs are now being sent and displayed in Kibana right away however, these logs are huge! And pretty useless obviously... I configured the template according to the guide but my log file is growing a lot every second. From 25 mb to 117 mb within a few minutes (from single end point) Please see this screenshoot - https://imgur.com/3wQmtpK
DeleteThere are mainly thousands entries related to C:\Windows\system32\wbem\wmiprvse.exe. I am not sure if I configured something in a wrong way. Please see the screenshoot of my Kibana - https://imgur.com/D9Vqk70
When I checked logstash logs (tail -f) I've seen there are some entries which are similar to what Kibana is displaying: https://imgur.com/Leg6Fjk
charlie@ubuntu:/var/log/logstash$ tail -f /var/log/logstash/logs*
UtcTime: 2018-01-06 20:22:44.291
SourceProcessGUID: {25851C25-60F3-5A51-0000-0010B05C0300}
SourceProcessId: 2308
SourceThreadId: 3808
SourceImage: C:\Windows\system32\wbem\wmiprvse.exe
TargetProcessGUID: {25851C25-60F1-5A51-0000-0010C32B0300}
TargetProcessId: 2152
TargetImage: C:\Windows\system32\svchost.exe
GrantedAccess: 0x1410
CallTrace: C:\Windows\SYSTEM32\ntdll.dll+5157a|C:\Windows\system32\KERNELBASE.dll+d817|C:\Windows\system32\wbem\cimwin32.dll+2a6c|C:\Windows\system32\wbem\cimwin32.dll+2291|C:\Windows\system32\framedynos.dll+84e0|C:\Windows\system32\framedynos.dll+914e|C:\Windows\system32\wbem\wmiprvse.exe+5f51|C:\Windows\system32\wbem\wmiprvse.exe+5cf0|C:\Windows\system32\RPCRT4.dll+323d5|C:\Windows\system32\RPCRT4.dll+269b2|C:\Windows\system32\ole32.dll+16f16e|C:\Windows\system32\wbem\FastProx.dll+d36d|C:\Windows\system32\ole32.dll+170ccd|C:\Windows\system32\ole32.dll+170c43|C:\Windows\system32\ole32.dll+2a4f0|C:\Windows\system32\ole32.dll+1714d6|C:\Windows\system32\ole32.dll+17122b|C:\Windows\system32\ole32.dll+16fd6d|C:\Windows\system32\RPCRT4.dll+250f4|C:\Windows\system32\RPCRT4.dll+24f56|C:\Windows\system32\RPCRT4.dll+2775b|C:\Windows\system32\RPCRT4.dll+2769b|C:\Windows\system32\RPCRT4.dll+27632|C:\Windows\system32\RPCRT4.dll+2532d], :response=>{"index"=>{"_index"=>"winlogbeat-2018.01.06", "_type"=>"doc", "_id"=>"AWDNI9xfO1U7sD6nOi79", "status"=>404, "error"=>{"type"=>"index_not_found_exception", "reason"=>"no such index", "index_uuid"=>"_na_", "index"=>"winlogbeat-2018.01.06"}}}}
Am I doing something wrong? I don't want to log unnecessary events like this. By the time I finish writing this post it generated THOUSANDS of entries lol. Thank you.
Hey Nieoceniony! If you feel that the the logs are useless because they are too big (showing unnecessary information) or there too many of the same kind and they are useless, you can do two things. First, create a logstash filter to strip fields content or remove fields to avoid having information that will not be useful in an engagement. Second, update the sysmon config that I provided in this post. I just provided a basic initial config that could help understand what you can log with Sysmon. Do those two things and see if all that helps your use case. I like to have as much data as possible first, and then I start filtering my logs depending on my use case. If this is for production, then you will have to make decisions on what you believe will reduce your false positive rates. I hope this helps. You are not doing anything wrong. This is the beginning of your own ELK build. Now you can make it your own and start creating your own configs. I am in the process of creating a DocckerFile for my own ELK: https://github.com/Cyb3rWard0g/HELK . That one will expedite building one and will have more advanced analytic capabilities to play with the data. There I have examples of Logstash filters and index templates. Dashboards are already created (default ones) and other enrichments are available.
DeleteThank you very much for the feedback nasreen!! It means a lot :) I am glad it is helpful. Let me know if there is anything that I should add or change or talk about more :) I hope you have a great weekend!
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteHi Cyberwardog, this post is super useful, I am excited to see the logs come in ELK and be able to run queries and start hunting. The setup worked as expected on Ubuntu 16.04 LTS assessing the ELK server through IP address. Could you please show how to configure it when accessing through DNS name instead of IP address? Thank you.
ReplyDeleteThank you so much for sharing this amazing blog, visit OGEN Infosystem for Website Designing Company in Delhi, India and also for SEO Service in Delhi.
ReplyDeleteWeb Development Company
I am Happy with your website. I got Lots of Knowledge in your site. I have shared your site to all. I have some site for all. Thank you.
ReplyDeleteAvast Login
garmin.com/express
avg.com/retail
bullguard login
mcafee.com/activate
Thank you for sharing this genuine blogspot with us. I like your post and now I am gone share it to my profile of facebook. Garmin Express by clicking on this link get know about me more.
ReplyDeleteThis is realy a Nice blog post read on of my blogs It is really helpful article please read it too my blog Change profile picture on Spotify. you can visits our websites or toll free no +1-866-558-4555. solve your problem fastly.
ReplyDeleteOn the topic of endpoint testing, have you tried google rapid response (GRR)?
ReplyDeleteThis series was extremely helpful to me in setting up a lab, and I would love to see new options/utilities
Buy Death Star
ReplyDeleteBuy Green Crack
Buy Zkittlez
Buy Ghost Train Haze
Buy Gorilla Glue
Buy Purple Kush
Buy Grape Ape
Buy adderall
ReplyDeleteBuy Xanax
Buy Methamphetamine
Buy alprazolam powder
Buy oxycontin
Buy Ketamine
McAfee activate
ReplyDeletemy.avast.com
Roadrunner Login
Netgear Login
BullGuard Login
Very Nice Blog and informative information...If you want to get to know more about How to fix Orbi Device Issues, then you can directly consult with Orbi Helpline experts. For any queries, call our experts at the USA/CA: +1-855-869-7373 and UK/London: +44-800-041-8324.
ReplyDeleteOrbi Helpline
Orbi Setup Issues
Tips to Fix Orbi Login and Setup Issues
How to Resolve The Netgear Orbi Error 404
How to Fix the Issue of Orbi Router Not Found
How to Fix Netgear Orbi App Login Error
How To Resolve The Error Of Orbi Firmware Update Error
How To Resolve The Netgear Orbi Authentication Error
How To Resolve The Netgear Orbi Certificate Error
Orbi Login and Setup Issues
Thanks for this informative information....If you are looking for how to resolve mcafee error 76567? No need to take worry, you can consult with our experts at USA/Canada: +1-855-869-7373 and UK/London: +44-800-041-8324. We are here to solve your antivirus issues.
ReplyDeleteHow to Resolve McAfee Error 76567
To have cyber security skills you need to undertake cyber security training. This is a training that is offered in a number of government and private institutions. cyber security institute in hyderabad
ReplyDeleteA debt of gratitude is in order for sharing the information, keep doing awesome... I truly delighted in investigating your site. great asset...
ReplyDeleteData Science Course
I truly like you're composing style, incredible data, thank you for posting.
ReplyDeleteData Science Training
I got my already programmed and blanked ATM card to withdraw the maximum of $50,000 daily for a maximum of 20 days. I am so happy about this because i got mine last week and I have used it to get $100,000. Skylink technologies is giving out the card just to help the poor and needy though it is illegal but it is something nice and they're not like other scam pretending to have the blank ATM cards. And no one gets caught when using the card. get yours today Just send them an email On skylinktechnes@yahoo.com whatsapp: +1(213)785-1553
ReplyDeleteGreat Article
ReplyDeleteArtificial Intelligence Projects
Project Center in Chennai
JavaScript Training in Chennai
JavaScript Training in Chennai
Welcome. DO NOT BE TROUBLED ANYMORE. you’re at the right place. Nothing like having trustworthy Hackers. have you lost money before or bitcoins and you are looking for a hacker to get your money back? You should contact us right away. It's very affordable and we give guarantees to our clients. Our hacking services are as follows:
ReplyDelete-Hack into any kind of phone
_Increase Credit Scores
_Western union, bitcoin and money gram hacking
_Criminal records deletion_BLANK ATM/CREDIT CARDS
_Hacking of phones(that of your spouse, boss, friends, and see whatever is being discussed behind your back)
_Security system hacking... and so much more. Contact THEM now and get whatever you want at
Email: atmgeniuslinks@gmail.com
Whatsapp: +1-(781)-656-7138.
WHY WOULD YOU NEED TO HIRE A HACKER:
There are so many Reasons why people need to hire a hacker, It might be to Hack a Websites to deface information's, retrieve information, edit information or give you admin access.
• Some people might need us To Hack Their Target Smartphone so that they could get access to all activities on the phone like , text messages , call logs , Social media Apps and other information's
• Some might need to Hack a Facebook , Gmail, Instagram , twitter and other social media Accounts,
• Also Some Individuals might want to Track someone else's Location probably for investigation cases
• Some might need Us to Hack into the Court's Database to Clear criminal records.
• However, Some People Might Have Lost So Much Funds With BINARY OPTIONS BROKERS or BTC MINING and wish to Recover Their Funds
• All these Are what we can get Done Asap With The Help Of Our Root HackTools, Special HackTools and Our Technical Hacking Strategies Which Surpasses All Other Hackers.
★ OUR SPECIAL SERVICES WE OFFER ARE:
* RECOVERY OF LOST FUNDS ON SCAM INVESTMENTS, BINARY OPTIONS TRADING & ALL TYPES OF INVESTMENT SCAMS.
* Credit Cards Loading ( USA Only )
* BANK Account Loading (USA Banks Only)
★ You can also contact us for other Cyber Attacks And Hijackings, we do All★
Whatsapp: +1-(781)-656-7138.
★ CONTACTS:
* For Binary Options Recovery, Feel free to contact us via Email: atmgeniuslinks@gmail.com for a wonderful job well done, Stay Safe.
IT HAS BEEN TESTED AND TRUSTED.
Welcome. BE NOT TROUBLED anymore. you’re at the right place. Nothing like having trustworthy hackers. have you lost money before or bitcoins and are looking for a hacker to get your money back? You should contact us right away. It's very affordable and we give guarantees to our clients. Our hacking services are as follows:Email:Creditcards.atm@gmail.com
ReplyDelete-hack into any kind of phone
_Increase Credit Scores
_western union, bitcoin and money gram hacking
_criminal records deletion_BLANK ATM/CREDIT CARDS
_Hacking of phones(that of your spouse, boss, friends, and see whatever is being discussed behind your back)
_Security system hacking...and so much more. Contact THEM now and get whatever you want at
Email:Creditcards.atm@gmail.com
Whats app:+1(305) 330-3282
WHY WOULD YOU NEED TO HIRE A HACKER??:
There are so many Reasons why people need to hire a hacker, It might be to Hack a Websites to deface information, retrieve information, edit information or give you admin access.
• Some people might need us To Hack Their Target Smartphone so that they could get access to all activities on the phone like , text messages , call logs , Social media Apps and other information
• Some might need to Hack a Facebook , gmail, Instagram , twitter and other social media Accounts,
• Also Some Individuals might want to Track someone else's Location probably for investigation cases
• Some might need Us to Hack into Court's Database to Clear criminal records.
• However, Some People Might Have Lost So Much Funds With BINARY OPTIONS BROKERS or BTC MINING and wish to Recover Their Funds
• All these Are what we can get Done Asap With The Help Of Our Root Hack Tools, Special Hack Tools and Our Technical Hacking Strategies Which Surpasses All Other Hackers.
★ OUR SPECIAL SERVICES WE OFFER ARE:
* RECOVERY OF LOST FUNDS ON BINARY OPTIONS
* Credit Cards Loading ( USA Only )
* BANK Account Loading (USA Banks Only)
★ You can also contact us for other Cyber Attacks And Hijackings, we do All ★
★ CONTACTS:
* For Binary Options Recovery,feel free to contact (Creditcards.atm@gmail.com)for a wonderful job well done,stay safe.
Why waste your time waiting for a monthly salary. When you can make up to $3,000 in 5-7days from home,
Invest $300 and earn $3,000
Invest $500 and earn $5,000
Invest $600 and earn $6,000
Invest $700 and earn $7,000
Invest $800 and earn $8,000
Invest $900 and earn $9,000
Invest $1000 and earn $10,000
IT HAS BEEN TESTED AND TRUSTED
Bitcoin investment has changed my life because I invested my bitcoin with Mr Carlos Oscar. He is a professional trader and he helps me trade my bitcoin and he can also help you. My first investment with Carlos Oscar , I profited up to $2000 with my investment of $200 in 7 days, Looking into this week as well, what have you planned to achieve? Why don't participate on this on going investment now and earn more money today if you are interested kindly contact Carlos Oscar via Email:tradewithcarlos2156@gmail.com or Text +15022064419
ReplyDeleteBitcoin investment has changed my life because I invested my bitcoin with Mr Carlos Oscar. He is a professional trader and he helps me trade my bitcoin and he can also help you. My first investment with Carlos Oscar , I profited up to $2000 with my investment of $200 in 7 days, Looking into this week as well, what have you planned to achieve? Why don't participate on this on going investment now and earn more money today if you are interested kindly contact Carlos Oscar via Email:tradewithcarlos2156@gmail.com or Text +15022064419
ReplyDeleteHello! This is my first visit to your blog! This is my first comment here, so I just wanted to give a quick shout out and say I genuinely enjoy reading your blog. It is rather a hassle-free process. But, yes, sometimes Garmin.com/Express users may faces certain issues. Connectivity issues are one of the most common issues that users face. If you are also wonder, why Garmin express update, then this piece of blog will provide a nice insight. We are available 24/7!
ReplyDeleteWe have seen many blog but this the great one, Thanks for provide great informatic and looking beautiful blog, really nice required information & the things i never imagined and i would like to request, wright more blog and blog post like that for us. Thanks you once agian
ReplyDeletebirth certificate in delhi
birth certificate in noida
birth certificate in ghaziabad
birth certificate in gurgaon
birth certificate agent in delhi
marriage registration in delhi
marriage certificate delhi
how to change name in 10th marksheet
marriage registration in ghaziabad
marriage registration in gurgaon
FRESH AND UPDATED STUFFS WITH 98% VALIDITY RATE ( DUMPS/ DUMPS+ATM PINS /CVV & fULLZ /, CC TOP UPS, BANK LOGS, VERIZON, PAYPAL ACCOUNTS, EGIFT CARDS FOR WALMART AND AMAZON AND SPAMMING TOOLS FOR SALE)
ReplyDelete..................................................................
ALL COUNTRY CREDIT CARDS and fullz...........
CCnum:: 4400663873545159
Cvv: 094
Expm: 06
Expy: 19 Fname: Gary
Lname: Hoskins
Address: 5830 Elwynn Drive
City: MILFORD
State: OH
Zip: 45150
Country: USA
Phone: 5138318649
Email: gch619@fuse.net
DEBIT : 432190 – 99, 445808, 450644, 450670, 451948, 454003, 458501, 471401, 472476, 486342, 503886, 522122, 528030, 529558, 531704, 531729, 539847, 545409, 551029
FULLZ
'''''''''''''
First Name : Kathryn
Middle Name : M
Last Name : Ratledge
Spouse Name : Ruth Ratledge
Father Name : Thomas Ratledge
Billing Address : 9 Ridgewood Dr
City : Greenville
State : CA
Zip Code : 29615
Country : US
Phone Number : 15629234492
Credit Card Information :
*********
Card Type : Credit
Credit Card Number : 4737033009002349
Exp. Date : 02/23
Name On Card : Kathryn Ratledge
Cvv2 : 736
ATM Pin: 5910
Bank Name : Bankk of America
Routing Number : 122000661
Account Number: 0222301305
Mother Maiden Name : Coleman
Social Security Number : 340224188
Birth Day : 19
Birth Month : 8/June
Birth Year : 1980
Account Information :
*******
AOL ID : Glendeweese
Password : BeenThere754
Account Open In: LD
Online ID: GROVANS11x
ATM or Check Card PIN: 001455
Passcode: eg17
......................................................................
DUMPS WITH PIN
Dumps + Pin ( USA )
Track1 : B4784559000586171^Andrew/Mayerbach^190310100000000000003343300003700000000
Track2 : 4784559000586171=19031010003343300003700
ATM Pin : 5241
------
Dumps + Pin ( Canada )
Track1 : B4530920124710013^Bibliotheque^2203220612800000054 7000000
Track2 : 4530920124710013=22032206128000547000
ATM Pin : 3377
If interested contact him as soon as possible via Email: atmgeniuslinks@gmail.com
WhatsApp: +1-781-656-7138.
https://goods4care.com/
ReplyDeleteBE SMART AND BECOME RICH IN LESS THAN 3DAYS....It all depends on how fast you can be to get the new PROGRAMMED blank ATM card that is capable of hacking into any ATM machine,anywhere in the world. I got to know about this BLANK ATM CARD when I was searching for a job online about a year ago..It has really changed my life for good and now I can say I'm rich and I can never be poor again. a family friend introduce us to them last year after i first sure the review online and my wife is a full house wife could not support looking for another good job was fucking hell, this hack card enables you to make withdraws on any ATM card in the world without having any cash in account or even having any bank account you can also use it to order items online, The least money I get in a day it is about $50,000.(fifty thousand USD) Even now and then I keeping pumping money into my account. Though it is illegal,there is no risk of being caught ,because it has been programmed in such a way that it is not traceable,it also has a technique that makes it impossible for the CCTVs to detect you. They also trade on bitcoin, For details on how to get yours today, email the hackers on (mrmichealblankatmcard@gmail.com)
ReplyDeleteAivivu chuyên vé máy bay, tham khảo
ReplyDeleteve may bay tet pacific airlines
vé máy bay đi Mỹ khứ hồi
ve may bay di Phap gia re
vé máy bay vietnam airline đi hàn quốc
vé đi nhật
mua vé máy bay đi Anh
trang web vé máy bay giá rẻ
READ CAREFULLY TO HELP SOMEONE
ReplyDeleteMy name is clara i'm from uk,i want to use this opportunity to disclose a vital information which I was asked not to.i have a brother who work as an anonymous he was the one who told me about this FREE CARD that you can used in buying and cash out a limit amount of money.he further told me their manager specialize in doing FREE CARD that he his going to send me his email but i should not expose him to manager in case he ask me how i got his email, that i found it on the internet so two days after i contacted him he reply was what's your name and how did you got my email which i told him exactly what my brother told me so after that he further asked me how he can be off help to me which i did by explaining my financial situation.After my explanation he asked some question which i answer then he reply by telling me he his a God fearing man that he was touch by my story that his going to help me.i was so happy he didn't rejected my offer. So after the interaction he ask me to give him some days that he will get back to me,then after a week interval in the morning i receive a package unknowingly to me he was the FREE CARD follow by the instruction how am going to register and used it.today making it a year plus that have been using this FREE CARD. NOTE;my major aim of revealing this information is because someone out there is passing through financial challenge you can as well reach him via email [officialfreecardmanager@gmail.com]
TRY YOUR LUCK WITH GOD ALL THINGS ARE POSSIBLE
I really appreciate the efforts of the writer as this post has written very carefully. Every piece of the sentence is systematically arranged and hence, one can easily understand the topic.Which country Netflix is the cheapest?
ReplyDeleteThank you for sharing this wonderful article.
ReplyDeleteSometimes Epson printer users might encounter the matter Epson Printer Not Printing throughout a print job. This can be the foremost common printing error faced by users. There's an added easy manner through that you'll get a reliable help. All you need to try and do is to place a call at Printer Customer Care and keep tuned with the technicians who answer your call.
Mua vé máy bay tại Aivivu, tham khảo
ReplyDeletevé máy bay đi Mỹ giá bao nhiêu
giá vé máy bay từ mỹ về việt nam
bay từ anh về việt nam
ve may bay tu phap ve viet nam
AOL Email login problems 2021 is very common. it shows that there is something wrong with the email account. here in this blog, I will assist you in fixing the problem. all you need to do, visit the askprob blogs to get the assistance.
ReplyDeleteNot receiving emails on hotmail. here are the steps to get that problem fixed. all you need to do, just make several changes into your account.
ReplyDeletemy husband and I are here to testify about how we used official hacking company ATM CARD to make money and also have our own business today. Go get your blank ATM card today and be among the lucky ones. This PROGRAMMED blank ATM card is capable of hacking into any ATM machine,anywhere in the world.It has really changed our life for good and now we can say we are rich and we can never be poor again. You can withdraw the manimum of $5,500 daily We can proudly say our business is doing fine and we have up to $ 1,000 000 (1 millions dollars in our account) Is not illegal, there is no risk of being caught, because it has been programmed in such a way that it is not traceable, it also has a technique that makes it impossible for the CCTV to detect you.. For details on how to get yours today, via E-mail: globalatmcardhackingservice@gmail.com
ReplyDeleteLove Quotes Hindi
ReplyDeleteDo you need an urgent loan of any kind? Loans to liquidate debts or need to loan to improve your business have you been rejected by any other banks and financial institutions? Do you need a loan or a mortgage? This is the place to look, we are here to solve all your financial problems. We borrow money for the public. Need financial help with a bad credit in need of money. To pay for a commercial investment at a reasonable rate of 3%, let me use this method to inform you that we are providing reliable and helpful assistance and we will be ready to lend you. Contact us today by email: daveloganloanfirm@gmail.com Call/Text: +1(501)800-0690 And whatsapp: +1 (315) 640-3560
ReplyDeleteNEED A LOAN?
Ask Me.
You can simply activate the FuboTV live streaming from Fubo.TV/connect, either through registered email ID or through FuboTV activation code.Login using the fubo.tv/Connect code which you get at the launch of the app.Hopefully, you would have learned the overall process to live stream your FuboTV. If you still have any doubt about the live streaming on your FuboTv or if you come across any error in FuboTV, then we are always available to assist you.
ReplyDeleteAre you looking for the instructions about AOL mail not working problem on iphone 2021? do not worry, here are the guide to fix that problem. you may apply it on your devices to get the proper solution. it will work fine on your devices.
ReplyDelete
ReplyDeleteOffice provides you a new way to create your own presentation or business. You can even make your own spreadsheets and presentations. It is the world’s most widely used software in every Pc or laptop or any other device.
Office.com/setup Home Student 2019 | Office.com/setup Home & Student 2019
Let’s talk about Lakewood Assisted Living. For that, you want to love where you are, who surrounds you, and what you’re doing. Sounds like The Gardens Care Homes Living Community in Pinehurst, NC. The living and community spaces are elegant with just-right warmth. There’s so much to do and share here, it’s a place where families can connect again. Moving to a senior living community is a big decision.
ReplyDeleteDo you know how to reset kindle fire password without losing data? If you want to know how to do this then get connected with us. Our team is very dedicated and skilled and will guide you in the best way. To know more check out the website Ebook Helpline.
ReplyDeleteDon’t know how to deal with the issue that the canon printer won't connect to wifi? Not to worry, we will assist you and offer you the best solution. We are a team of skilled and highly educated technicians, who works at day as well as night to provide you best service. To know more check out the website Printer Offline Error.
ReplyDeleteYour blog is filled with unique good articles! I was impressed how well you express your thoughts.
ReplyDeleteE Sathi | E Sathi UP
Your Information is so amazing. I appreciate your hard work and your skills. Thank you for sharing this information with us.
ReplyDeleteHot Rolling Mill Manufacturer In India
Hot Rolling Mill Manufacturer
Rolling Mill Manufacturer in India
Rolling Mill Manufacturer
Hot Rolling Mill
Thanks for sharing an informative post. Keep on sharing such useful information.
ReplyDeleteUiPath Training In Bangalore | UiPath Online Training
AS400 Training In Bangalore | AS400 Online Training
Docker and Kubernetes Training In Bangalore | Docker and Kubernetes Online Training
Go Language Training In Bangalore | Go Language Online Training
Oracle Apps Technical Training In Bangalore | Oracle Apps Technical Online Training
UI UX Design Training In Bangalore | UI UX Design Online Training
Pyspark Training In Bangalore | Pyspark Online Training
React Native and Redux Training In Bangalore | API Online Training
Adobe Sitecatalyst Training In Bangalore | Adobe Sitecatalyst Online Training
Python with Django Training In Bangalore | Python with Django Online Training
I read your post. It is really so informative information. Thanks for sharing.
ReplyDeleteContinuous Shear is manufactured and exported by Akshi Engineers Private Limited is a major producer and exporter. We made continuous shear, which is highly demanded in the market due to its superior efficiency. Our shears are made according to industry norms, under the supervision of skilled technicians, using high-quality materials and state-of-the-art technologies.
There Is No Muddled Method Here. It Is Appropriate To Take Note Of That When You Type "Bellsouth Email Login Page" On The Google Search Box, You Will Be Diverted To The Att Site. This Occurs With All Clients Who Attempt To Make A Bellsouth Email Account.
ReplyDeleteCrawl Info
looking for solutions? you can wait for a few minutes or hours and then log back in and you will be able to log in if there was a temporary connectivity issue.
ReplyDeleteHulu Activate |
www.hulu.com/activate |
192.168.0.1 is the default gateway that is used by routers and modems such as D-Link as default IP address for logging the admin panel.
ReplyDelete192.168.0.1 | 192.168.1.1
Thanks for sharing your amazing thoughts. It's a well-explained and informative blog.
ReplyDeletemailsbug.com
nice post.best aws training
ReplyDeleteDo you need an urgent loan of any kind? Loans to liquidate debts or need to loan to improve your business have you been rejected by any other banks and financial institutions? Do you need a loan or a mortgage? This is the place to look, we are here to solve all your financial problems. We borrow money for the public. Need financial help with a bad credit in need of money. To pay for a commercial investment at a reasonable rate of 3%, let me use this method to inform you that we are providing reliable and helpful assistance and we will be ready to lend you. Contact us today by email: daveloganloanfirm@gmail.com Call/Text: +1(501)800-0690 And whatsapp: +1 (501) 214‑1395
ReplyDeleteNEED A LOAN?
Ask Me.
We can proffer you with the assistance to set up your printer. If you are getting the message like Printer Is Offline, then visit our website. After that, follow the given steps to resolve this issue. We assure you that if you followed the proper steps one by one, your issue would be resolved.
ReplyDeletehttps://www.printerofflinefix.net
We can fix all of the problems that are plaguing Att Yahoo Mail. If you're having issues sending and receiving emails from your SBCglobal Yahoo mail, the best thing you can do is get SBC electronic mail assistance from our professionals. You have two options: log on and look for the steps there, or call us at our SBCglobal electronic number.
ReplyDeleteFor more details visit our website:
https://www.sbcgloballogin.com/sbcglobal-att-net-email-login/
Thank you for posting this great article! You did a wonderful job. Keep it up.
ReplyDeleteData Science Training in Hyderabad
Data Science Course in Hyderabad
Awesome post! Your post is well-written. It is really an informative post for me.
ReplyDeleteThank you for giving me this information.
Akshi Engineers design the high quality products with entire features to the Rolling Mill. We offer conceptual design to Mill Stand as per client requirements. We provide conceptual design to Mill Stand as per the requirements of the client. At an affordable cost, we implement custom solutions in the market. To get one stop solution for mill stand, just dial our toll-free number +91-98106-62353.
You can make video how you setting this up and publish it on tiktok or youtube. From this site https://soclikes.com/ you can get many likes for your video
ReplyDeleteThank you for posting such a great article! It contains wonderful and helpful posts. Keep up the good work
ReplyDeleteMera Ration App, Mera Ration App Download, Benefits, Login and Registration
Great Information. Thanks for giving me this information. Keep sharing again.
ReplyDeleteWhen you have water damage issues in your homes, such as flooding from broken or leaky pipes, frozen pipe water damage, sink overflow, toilet overflow, bathtub overflow, refrigerator, washing machine, water heater, or dishwasher overflow, air conditioner leaks, sump pump failure, hardwood floor water damage, or basement water damage, our professional team can remove any water-damaged mats. Whatever the extent of your flood damage, we have a viable solution for you. Home In Home Remodel and Repair LLC is an excellent local service provider of Water Damage Stanwood WA. When you work with us, you get the finest solution to water restoration. To get the best solutions for water damage repair, just dial our toll-free number. We will guide you in the right way.
Informative Post. Thanks for giving me this information. Keep on Posting.
ReplyDeleteTodd Peters Electric offers the best Electrician Riverside CA. We provide a wide range of electrical services to residents near Riverside County. If you need repair or remodeling in your home, you can contact our professionals. We are always available to assist you.
Thanks for your marvelous posting! I really enjoyed reading it, you could be a great author. I will be sure to bookmark your blog and definitely will come back in the foreseeable future. I want to encourage you to continue your great posts, have a nice afternoon!
ReplyDeleteDigital Marketing Course in Bangalore
There is an inborn curiosity about the marriage prediction free as per your date of birth and name, and we can do it for you. Click here to know when When I Will Get Married and how will be married life in the future according to your birth-chart. You can also book a direct appointment to ask any query regards marriage.
ReplyDeleteAmazon prime can be found to owners through amazon com/mytv of flowing programs and apparatus. On amazon prime you are able to stream movies and television episodes on amazon video program. You can enjoy amazon prime video on different platforms like fire television, smart-tv, streaming media player, video games console, cell phone or tablet computer. You can easily activate your amazon prime you just need to follow the simple instructions and go to www.amazon.com/mytv to activate amazon Prime Video on your TV. You just need to enroll your compatible device at mazon.com? Just go to the site www.amazon.com/mytv and observe the guidelines to fill out the enrollment of your device, then it is possible to begin appreciating Amazon Prime Instant Video service for free. You need to make use of the 6 digit amazon MY TV code to get enrollment of one’s apparatus.
ReplyDeleteReach out us:
a href="https://mytvlink-code.com/amazon-com-mytv/">www.amazon.com/mytv</a
Very userful info, thanks to author. Don't you think it's worth posting these thoughts on Instagram? After all, this social network is now very popular. By the way, I advise you to use https://viplikes.net/ in order to quickly increase the number of followers and promote your account to the top.
ReplyDeleteIf you are worried about your Canon printer and looking for a site where they taught you how to change ink in a Canon printer then you have to follow some steps to change the ink and you also have to visit the main sites of canon.
ReplyDeleteAmbien is a
ReplyDeleteprofessionally prescribed medicine accessible in quick delivery and
controlled delivery plans, order ambien
Buy Ambien 10mg Online.
Straightforward Online Pharmacy is an enlisted UK online drug store and specialist.
We give a scope of medicines and Buy ambien online
specialist meetings
Is your Quickbooks giving you troubles these days? Are you not able to use one or more of its features? Don’t worry; you have quick resolution for these issues on your own phone. Just dial +1(830) 476-2055 to reach our Quickbooks supportcenter. Talk to our engineer and get solutions for all your issues related to Quickbooks.
ReplyDeleteWebroot.com/safe provides full security of cyber threats and speeds up the user's device/system. They users who have bought Webroot Antivirus software need to activate the software on their system or device via www.webroot.com/safe.
ReplyDeleteYou can read sites with interesting pragamtic slot game articles, by reading the sites I recommend below you will understand the true meaning of the word slot game.
ReplyDeleteslot bonanza
slot deposit via shopeepay
pragmatic play deposit pulsa telkomsel
cara deposit slot bca
cara deposit slot bca
cara daftar slot pragmatic
daftar aztec game/
https://103.214.113.98/
juarabet99
link slot pragmatic idr
Some professional training companies even have their test materials endorsed from Cisco, which they give to the students for a price. These tests tend to be the most realistic exam simulations with item types unique to every exam (case studies, active screen, drag and drop, hot area, multiple choice, free response, etc.). CCNA Training in Pune
ReplyDeleteNice blog get the best Shayari
ReplyDeletewhen you update your McAfee not Responding it is possible to face some server error like "McAfee is unable to update your software. Check your internet connection" Then, your "McAfee Antivirus Not Responding update has stopped at zero or at some random percentage" or similar.
ReplyDeleteबड़ा आसान है कंप्यूटर से फेसबुक अकाउंट को डिलीट करना, बस फॉलो करने होंगे ये स्टेप्स Read More
ReplyDeleteNews Website
News website profile
News website comments
Vidrohi aanand
Vidrohi Anand
Anand news
Latest News
Cricket News
Exam News
It's a really great and useful piece of information. Thanks, and please keep sharing again.
ReplyDeleteManali is considered the most important hill station but the journey might be easier with appropriate guidelines. You can contact Manali Tourism consultants to know about the right season to visit and also what would be the cost-effective ways to travel over there. Your planned system will let you make fun without any stress and also you would be able to create recollections.
I read your post. It is amazing and helpful information for me. Thanks for sharing with everyone .ATT is the wor s your data from unwanted people and viruses. If you are an ATT user, and, while using an ATT email account, you are troubled by ATT Email Login issues. You don't need to worry, in this case, you just need to dial our ATT customer care number and they will provide accurate solutions regarding problems.
ReplyDeleteThank you for sharing such a great post. Keep it up.
ReplyDeleteAre you looking for help to unlock the Yahoo account? Is the technical issue of the Yahoo account setting bothering you? You need to avail Yahoo Help that is accessible around the clock. The technical team of Yahoo ensures immediate support for the rectification of the technical problems.
Awesome post! Your post is well-written. It is really an informative post for me. Thank you for giving me this information.
ReplyDeleteAkshi Engineers design high quality products with entire features to the Rolling Mill. We offer conceptual design to Mill Stand as per client requirements. We provide conceptual design to Mill Stand as per the requirements of the client. At an affordable cost, we implement custom solutions in the market. To get a one-stop solution for the mill stand, visit our website.
MediGlow Healthcare is one place that tries to put its every effort into being an efficient healthcare system contributing an important part in the country’s development, economy, and promoting the physical and mental health being of people around the world. Healthcare has always been regarded as an integral part of the whole system as the quality of life is very important and helps people all around with different kinds of solutions.
ReplyDeleteExample Services :-
Hair Transplant
Hydra facial
Eyebrow Microblading
Acne, Scar treatment
Hair PRP
Chemical peel
Medical Cosmetology/Aesthetic Physician
General Physician
Thanks for giving me this information. Keep posting again.
ReplyDeleteCoin Master Free Spins is one of the thrilling and entertaining games. You can play this game easily and get coin master free spins and links. If you don't know how to get a 1k Free Spin Coin Master easily? For more information, you can visit our website.
izmit eskort
ReplyDeletekarabük eskort
karaman eskort
karşıyaka eskort
kastamonu eskort
kayseri eskort
kırıkkale eskort
kırklareli eskort
kırşehir eskort
konya eskort
rize eskort
ReplyDeletesakarya eskort
samsun eskort
sinop eskort
sincan eskort
şile eskort
tekirdağ eskort
trabzon eskort
yalova eskort
zonguldak eskort
ayvalık eskort
ReplyDeletebalıkesir eskort
bilecik eskort
bolu eskort
bursa eskort
çankırı eskort
çeşme eskort
çorlu eskort
didim eskort
düzce eskort
çanakkale eskort
ReplyDeleteyozgat eskort
nevşehir eskort
gümüşhane eskort
kütahya eskort
tokat eskort
bayburt eskort
beylikdüzü eskort
istanbul eskort
eskişehir eskort
ReplyDeletefethiye eskort
gaziemir eskort
gebze eskort
giresun eskort
görükle eskort
hatay eskort
iskenderun eskort
ısparta eskort
izmir eskort
sivas eskort
ReplyDeletetekirdağ eskort
tokat eskort
trabzon eskort
tunceli eskort
urfa eskort
uşak eskort
van eskort
yalova eskort
yozgat eskort
burdur eskort
ReplyDeletebursa eskort
çanakkale eskort
çankırı eskort
çorum eskort
denizli eskort
diyarbakır eskort
düzce eskort
edirne eskort
elazığ eskort
adana eskort
ReplyDeleteadıyaman eskort
afyon eskort
ağrı eskort
aksaray eskort
amasya eskort
ankara eskort
antalya eskort
antep eskort
ardahan eskort
nevşehir eskort
ReplyDeleteniğde eskort
ordu eskort
osmaniye eskort
rize eskort
sakarya eskort
samsun eskort
siirt eskort
sinop eskort
şırnak eskort
izmir eskort
ReplyDeletemaraş eskort
karabük eskort
karaman eskort
kars eskort
kastamonu eskort
kayseri eskort
kilis eskort
kırıkkale eskort
kırklareli eskort
artvin eskort
ReplyDeleteaydın eskort
balıkesir eskort
bartın eskort
batman eskort
bayburt eskort
bilecik eskort
bingöl eskort
bitlis eskort
bolu eskort
eskişehir eskort
ReplyDeleteerzincan eskort
erzurum eskort
giresun eskort
gümüşhane eskort
hatay eskort
ığdır eskort
ısparta eskort
istanbul eskort
izmir eskort
niğde eskort
ReplyDeleteordu eskort
osmaniye eskort
rize eskort
sakarya eskort
samsun eskort
siirt eskort
sinop eskort
şırnak eskort
sivas eskort
tekirdağ eskort
ReplyDeletetokat eskort
trabzon eskort
tunceli eskort
urfa eskort
uşak eskort
van eskort
yalova eskort
yozgat eskort
zonguldak eskort
**SSN FULLZ WITH HIGH CREDIT SCORES AVAILABLE**
ReplyDelete>For tax filling/return
>SSN dob DL all info included
>For SBA & PUA filling
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING CARDING CASHOUTS CLONING**
=>Contact 24/7<=
Telegram > @killhacks
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
FRESHLY SPAMMED
VALID INFO WITH VALID DL EXPIRIES
*All info included*
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
CC & CVV'S ONLY USA AVAILABLE
SSN+DOB
SSN+DOB+DL
High credit fullz 700+
(bulk order negotiable)
*Payment in all crypto currencies will be accepted
->You can buy few for testing
->Invalid info found, will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS AVAILABLE FOR
(Carding, spamming, hacking, scripting, scam page, Cash outs, dumps cash outs)
Ethical Hacking Tools & Tutorials
Kali linux
Facebook & Google hacking
Bitcoin Hacking
Bitcoin Flasher
SQL Injector
Bitcoin flasher
Viruses
Keylogger & Keystroke Logger
Logins Premium (Netflix, coinbase, FedEx, PayPal, Amazon, Banks etc)
Bulk SMS Sender
Bitcoin Cracker
SMTP Linux Root
DUMPS track 1 and 2 with & without pin
Smtp's, Safe Socks, rdp's, VPN, Viruses
Cpanel
PHP mailer
Server I.P's & Proxies
HQ Emails Combo (Gmail, yahoo, Hotmail, MSN, AOL, etc)
->Serious buyers are always welcome
->Big discount in bulk order
->Offer gives monthly, quarterly, half yearly & yearly
->Hope we do a great business together
CONTACT 24/7
Telegram > @killhacks
ICQ > 752822040
Skype > Peeterhacks
Wickr me > peeterhacks
ReplyDeleteHOW I MADE THOUSANDS OF DOLLARS WITH $1,000 VIA BITCOIN TRADING EXPERT
It's been more than a month of constant happy returns from all the investments I have made with David Benjamin after a saw a review on Quora. My first investment of $1,000 got me $9,300 in an amazing few days. I saw a few reviews on here and decided to add mine to guide and inspire someone to make that right decision to invest and trust this expert trader with skills and enhanced software to navigate the market. Contact on davidbenjaminexptrader@outlook.com or on WhatsApp +1 408 500 0775
ReplyDeleteThanks for sharing such an awesome blog.
30% Discount on reservations for Delta First Class Seats
For pro conveniences, recreation, and prevalent administrations, you won't see as anyplace other than Delta Airlines First Class Seats. You'll encounter Sky Priority administration all through your outing. Furthermore, there are different advantages that won't stop all things considered.
So if you want guaranteed airline discount on tickets for Delta First Class Seats please visit our site
"Delta First Class Seats
" or call us at 1-855-915-0936
Hi there!
ReplyDeleteI had a very nice experience in your blog, actually I found this post explanatory and informative, keep sharing the best content
regards
Salvatore from Visite as Cataratas do Iguaçu em Foz do Iguaçu, Paraná - Brasil.
Thanks and take care
Thank you for your articles that you have shared with us. Hopefully you can give the article a good benefit to us. Delta 8 thc buy
ReplyDeletePython is an open-source programming language that is multifaceted and object-oriented. It sounds tricky, but it is one of the easiest languages because of the simple syntaxes. And this ease has made it ubiquitous in several companies. So, Cyber Success has come up with a Python training in Pune wherein we cover all fundamentals of Python, data structures, modules, Data Science, and much more. Python Training in Pune
ReplyDeleteDesiwedlocks is a Matchmaking services that offers the best matrimonial services. Because it is an open and free platform, anyone can join. Hundreds of thousands of people have found their life partner through our groundbreaking matchmaking service, and countless others have made some very special friends. Desiwedlocks understands the significance of selecting the right partner for a wedding, particularly in the Indian cultural context.
ReplyDeleteHealthy life Human provides general information on everything like health and lifestyle, human diseases, travel, career, business etc. We provide correct and reliable information the audience.
ReplyDeleteYou have truly inspired me and I am delighted to have access to this special site today. A wonderful and inspiring effort in your article. Thank you very much for sharing a helpful post. stars polytechnic admission form
ReplyDeleteBy the way, in one of the hacks, you might have to use the Netgear Orbi router login credentials. Thus, keep them jotted down on a piece of paper. Continue reading.
ReplyDeleteGreat Blog.Thanks for posting.
ReplyDeleteCCNA course in Pune
keka login
ReplyDeletenice blog
ReplyDeleteCCNA classes in Pune
click bank
ReplyDeletecontact SBCGlobal Email Support, there are a few methods you can try. Firstly, you can call their customer support phone number, which can usually be found on the AT&T website or in your account details. Another option is to visit the AT&T Support website or the SBCGlobal email support page and utilize their online support options such as live chat or submitting a support ticket.
ReplyDeleteSBCGlobal Support Number
Tomamos la goma y marcamos un punto en ella con un rotulador, para que nos sirva de referencia. Colocamos la goma dentro상주출장샵 del tubo de plástico y la sujetamos con el tapón de corcho, de forma que el punto de referencia próximo al comienzo del gancho. Este será el cero de la escala.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteName : Rajaji Curry House Indian Restaurant
ReplyDeleteAddress: 2603 Connecticut Ave NW #2634, Washington, DC 20008
Phone: +12022657344
Rajaj Ji is your ultimate destination for an unparalleled Indian dining experience in Washington, DC. Situated in the vibrant culinary scene of the city, our restaurant is a beacon for those seeking the finest Indian flavors. With a menu curated to perfection, we offer a symphony of tastes and aromas that showcase the essence of Indian gastronomy. From classic favorites like butter chicken to regional specialties like biryani, each dish is a masterpiece crafted with care and expertise. Our commitment to using authentic spices and fresh ingredients ensures an unforgettable dining journey that celebrates the Best Indian Food in WASHINGTON, DC. Whether you're a connoisseur of Indian cuisine or a first-time explorer, Rajaj Ji promises a culinary adventure that will leave you craving for more. Experience the magic of Indian cuisine at Rajaj Ji today.
Rook piercing benefits include reduced migraines, enhanced ear aesthetics, and a unique style statement. It's a cartilage piercing that can alleviate pressure points associated with headaches. Additionally, it offers a fashionable and distinctive look, setting you apart.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteAirlineTerminalInfo is a fantastic resource for travelers. It provides real-time updates on gates, terminals, and airport services, ensuring you stay informed throughout your journey. Whether you're flying for work or leisure, this tool helps reduce the stress of navigating airports. A must-have for anyone looking to make their airport experience as smooth as possible!
ReplyDeleteKegel balls at Cupidbaba are designed to help improve pelvic floor strength and enhance intimate pleasure. Available in various sizes and materials, these balls are perfect for both beginners and experienced users. Regular use may improve muscle tone, leading to better control and intensified sensations.
ReplyDeleteAre you looking to step into the world of forex trading without risking your own capital? WinproFX offers a Free Funded Forex Account, giving traders the opportunity to access real trading capital and experience the live markets without an initial deposit. This unique funding program is designed for skilled traders who want to prove their abilities and grow their portfolios. By trading with WinproFX’s funded account, you can take advantage of real-time market conditions, advanced trading tools, and flexible leverage to maximize your potential profits. Whether you're a beginner looking to gain experience or a seasoned trader aiming to scale up, this funded forex account is the perfect gateway to financial independence.
ReplyDeleteWinproFX ensures that traders receive top-tier trading conditions, including tight spreads, fast execution speeds, and access to major currency pairs and commodities. With their Free Funded Forex Account, you don't have to worry about the initial investment—simply focus on executing profitable trades and meeting the performance criteria. If you successfully meet the requirements, you can withdraw your profits and even qualify for higher funding levels. This program is a game-changer for traders who lack the capital but have the expertise to thrive in the forex market. Don’t miss this opportunity—sign up with WinproFX today and start trading with a funded account!
Free Funded Forex Account-
This process reminded me of the importance of having a reliable partner for managing and updating content. A Digital Services Agency can be an invaluable resource in such situations. Whether it’s updating technical guides, refreshing visuals, or ensuring your content remains relevant and accurate, a content creation agency handles the heavy lifting.
ReplyDeleteThank you so much for sharing this valuable information! It’s really helpful and insightful. I appreciate the effort you've put into explaining things so clearly. Looking forward to reading more of your posts! Near me
ReplyDeleteTechndsoft
Tech Towns
ReplyDeleteThanks for this information! It's really helpful and provides great insights. I appreciate you sharing it!
kw
kw
kw
kw
kw
kw
HOW I RECOVER MY $275,000 FROM CBEX
ReplyDeleteI’m one of the fortunate individuals who ventured into the cryptocurrency market with hopes of building a nest egg for retirement. Sadly, I invested in a fraudulent platform that ended up scamming me out of approximately $275,000, not including the promised profits. I lost everything, including funds borrowed from friends in my investment quest. Just when I thought all was lost, I discovered the cryptocurrency recovery experts at JetWebHackers. They successfully helped me recover my funds within 72 hours, and I was even able to track down the scammers. I am incredibly thankful for their assistance and strongly recommend their services to anyone facing a similar situation.
Reach out to them today and turn your situation around!
WEBSITE: jetwebhackers. com
EMAIL: jetwebhackers@gmail.com
Telegram: @jetwebhackers
WhatsApp: +1 (310)721-3656
I can’t wait to apply some of these takeaways in my own work. If you’re interested in exploring more content like this, I’d love to invite you to check out my website FuboTV offers various add-ons including premium channel packages like Paramount+ with SHOWTIME, MGM+, and STARZ, as well as sports add-ons such as NBA League Pass, Sports Plus with NFL RedZone, and MLB.TV FuboTV6 is compatible with the majority of Roku devices, including streaming sticks, Roku TVs, and Roku players.
ReplyDeletefubotv/link6
fubo.tv/link6.
fubotv/roku-connect
peacocktv.com/tv
Omega Astro is your one-stop shop for comprehensive astrology services to the cosmos, blending the ancient wisdom of astrology with modern insights to illuminate your life's path. We specialize in crafting personalized birth chart readings, in-depth horoscope analyses, compatibility insights, and predictive guidance—all tailored to your unique journey. With the best online astrology consultation in India, you gain not just knowledge but spiritual empowerment to make informed decisions, overcome challenges, and embrace your destiny. Trust us as your celestial companion, guided by the stars and grounded in the divine wisdom that has guided humanity for millennia.
ReplyDeletecareer astrology service || finance prediction astrology || medical astrology consultation
Looking for trusted guidance from a well-known astrologer? Chandigarh is home to several reputed names, but Omega Astro stands out as a celebrity astrologer in Chandigarh known for accurate predictions and deep expertise in Vedic astrology. With years of experience and a client base that includes celebrities, professionals, and NRIs, Omega Astro offers insights on career, marriage, education, and foreign travel astrology by date of birth. Their personalized consultations, scientific approach, and use of modern tools make them a top choice for astrology services. Whether it's Kundli analysis or life predictions, Omega Astro is a trusted name in the region.
ReplyDeleteLooking for a reliable SEO company in Wichita to boost your online visibility and grow your business? A trusted SEO partner can help your website rank higher on search engines, attract targeted traffic, and convert visitors into loyal customers. Whether you're a local business or a growing enterprise, investing in professional SEO services ensures you're staying ahead of the competition. From keyword research to on-page optimization and link building, a dedicated SEO company in Wichita can tailor strategies to fit your unique goals. Make your digital presence stronger and drive real results with expert SEO support customized for Wichita businesses.
ReplyDeleteEnhancing endpoint visibility is crucial for cybersecurity, just like maintaining a clean environment is essential for your workspace. With expert services from Pest Control Ottawa, you can focus on threat detection without worrying about unwanted intrusions from pests. Choose Pest Control Ottawa to safeguard both your systems and your space. Visit on https://qpcottawa.com/
ReplyDeleteGreat insights on using Sysmon for endpoint visibility and ELK stack integration! Just like cybersecurity requires proactive monitoring, homes need preventive care too. That’s why I always recommend Ottawa Pest Control for reliable solutions—keeping pests away before they become a problem. Prevention truly saves time and stress! Visit on https://a2zpestcontrol.ca/
ReplyDeleteGreat insights on endpoint visibility and Sysmon setup! Just like filtering noise in logs, Ottawa Pest Control helps eliminate unwanted pests effectively. With reliable pest management, you can focus on advanced tasks without distractions. A pest-free environment ensures comfort, safety, and productivity—perfect for both home and workspace needs. Visit on https://a2zpestcontrol.ca/
ReplyDeleteGreat insights on using Sysmon and Winlogbeat for endpoint visibility! Just like monitoring systems protect networks, Raccoon Removal Ottawa protects homes from intruding wildlife. Both require the right tools and expertise to ensure safety and reliability. Stay secure—whether it’s defending against cyber threats or unwanted raccoons in Ottawa. Visit on https://qpcottawa.com/raccoon-removal-ottawa-safe-humane-wildlife-control-by-quick-pest-control-ottawa/
ReplyDeleteApparelnBags is a trusted destination for quality apparel, uniforms, and accessories at affordable wholesale prices. The company partners with well-known brands that deliver comfort, style, and durability. Customers can explore premium Sport Tek apparel
ReplyDeletedesigned for teams, athletes, and active lifestyles. With competitive rates, fast delivery, and excellent service, ApparelnBags makes bulk shopping simple. The collection features versatile performance wear, casual basics, and fashion-forward options. As a reliable wholesale supplier, ApparelnBags helps customers save more while upgrading their wardrobe.
ACSIUS is a premier Pay per Click (PPC) management company in India, specializing in precision-driven ad campaigns across Google Ads, Bing, and social platforms.
ReplyDeletePPC Company India
Apkwhatsb provides the latest GBWhatsApp features with better privacy controls, customization options, and smooth performance. The site offers updated GB WhatsApp APK downloads along with clear installation guides, feature explanations, and update details. Users can explore new themes, advanced settings, and secure chat options in one place. For safe and reliable GB WhatsApp versions, visit https://Apkwhatsgb.com
ReplyDeleteAOL Desktop Gold not printing is a common issue faced by users when documents, emails, or web pages fail to print properly. This problem may occur due to outdated printer drivers, incorrect printer settings, connectivity issues, or software glitches within AOL Desktop Gold. Troubleshooting steps like checking printer configuration, updating drivers, restarting the application, and reinstalling AOL Desktop Gold can help restore normal printing functionality quickly.
ReplyDeleteIf your Canon printer keeps going offline , it may be due to network issues, outdated drivers, incorrect printer settings, or Windows errors. Learn the common causes and step-by-step solutions to bring your Canon printer back online and ensure smooth, uninterrupted printing.
ReplyDelete